As the conflict between Russia and Ukraine intensified, the hacking team began to join the team. On Feb. 25, core members of the Conti ransomware organization posted a radical pro-Russian message on their official website saying they would fully support the Russian government and threatening to launch a cyberattack against any hacker who attacked Russia.
Pictured: Conti organization's statement in support of Russia
The news appeared to infuriate a Ukrainian security researcher. On Feb. 27, the researchers hacked into the gang's internal Jabber/XMPP servers and emailed internal logs to multiple journalists and security researchers, while over the next few days the members released a large amount of Conti internal data. The leaked data is shown in the following table.
Table: Data breach timeline
Anheng Hunting Laboratory analyzed some of the major leaked documents.
01
Chat history
The original leaked documents, leaked by email to journalists and security researchers on Feb. 27, contained 339 json files stolen from Conti's Jabber servers, each containing a full day of chat history spanning From January 29, 2021 to February 27, 2022, and the researchers have confirmed the authenticity of the conversation.
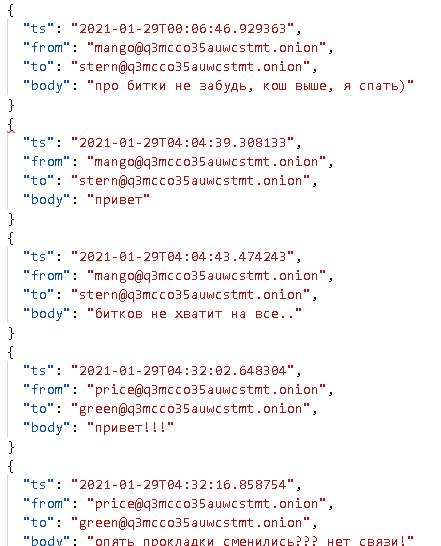
Figure: Chat history specifics
From the chat history, we can find a lot of valuable information, including:
The names of the members of Conti within the organization
Reveals conti's ties to the TrickBot and Emotet malware gangs, which often lease access to infected computers from the latter to deploy their malware
Confirm that the TrickBot botnet was shut down earlier this month
Some undisclosed ransomware incidents
More than 200 Bitcoin addresses of the Conti organization
The internal workflow of the organization
TTP organized by Conti
......
The researcher continued to update the chat history, even including the chat history of the Conti organization after the data was leaked.
02
Conti source code
The personnel initially leaked an encrypted package that included the source code of the three components, buildter, decryptor, and locker, without giving a password, claiming to prevent excessive damage; but then he leaked a source code package without a password and deleted the implementation code of the locker component.
Figure: The member refuses to provide the package password
03
Internal component code
Much of the code Conti uses appears to be open source software, such as the two PHP frameworks, yii2 and Kohana, which are used as part of the admin panel code.
Figure: Exploitation of the Code of the Yii Framework
04
Leaked IOC summary
Hunting Labs summarized the IOC generated by this leak. For details, please refer to the appendix. The value of these IOCs is shown in the table below.
Note: This article is reported by E Security Compilation.