In 2021, the Ministry of Public Security deployed the national public security organs to deepen the promotion of the "Clean Net 2021" special action, launched the "four breaks" action of breaking black cards, black numbers, black lines, and black equipment, dynamically studied the trend of network violations and crimes, deeply analyzed the characteristics of network violations and crimes, severely cracked down on online gambling, network hacking, infringement of citizens' personal information and other activities, continued to strengthen the governance of cyberspace order, and created a safe, clear and orderly network environment. On December 22 of the same year, the Central Cyberspace Administration of China launched the special action of "Clear And Clear, Crack down on traffic fraud, black public relations, and online water army".
With the innovation and upgrading of Internet technology, new forms of cybercrime emerge in an endless stream, and "black and gray production" has shown a development trend of industrialization. At present, the mainland's "black and gray production" has formed a huge "black gold" interest chain with an annual output value of 100 billion yuan and more than 1.5 million employees. From the secret deduction of phone bills, the realization of advertising traffic, the distribution of mobile applications, to the "Trojan horse" brush volume, ransomware, and control of "broiler" mining, "black ash production" has a variety of forms, and "wool" is one of its important profit models. Starting from the actual situation, starting from the perspective of common types of "black ash production", this paper deeply analyzes the industrial chain structure of "black ash production", analyzes the problem of "black ash production" from the perspective of the communication industry, and puts forward suggestions for the communication industry to adopt digital and intelligent methods for early warning and prevention and control of "black ash production".
"Black ash production" industrial chain structure
"Black ash production" refers to telecommunications fraud, phishing websites, Trojan horses, hacker extortion and other acts that use the Internet to carry out illegal and criminal activities. Among them, "black industry" refers to the network crime of direct contact with national laws; "gray production" is a controversial behavior that travels on the edge of the law and provides auxiliary means for "black industry".
With the expansion of the Internet from the PC end to the mobile end, "black ash production" has also developed from the earliest control of "PC weak chicken" to the current attack on various apps on the mobile Internet, and the attack scenarios are concentrated in the e-commerce platform "Xue Wool", bank financial fraud, live broadcast platform brushing, advertising brush volume, social platform brush powder, traffic fraud, fission promotion, platform pulling, network fraud, etc., involving all walks of life in society, and the specific operation actions change with the type of attack, causing great harm to society.
First, the division of labor in "black and gray production" is meticulous, clear and secretive
"Black ash production" is a very secret underground industry, and the sources of funds, cooperation models, business models, realization channels, and profit distribution models are not well known. At present, the "black and ash production" industrial chain that has been explored includes three links: resources, services and realization, as shown in Figure 1.
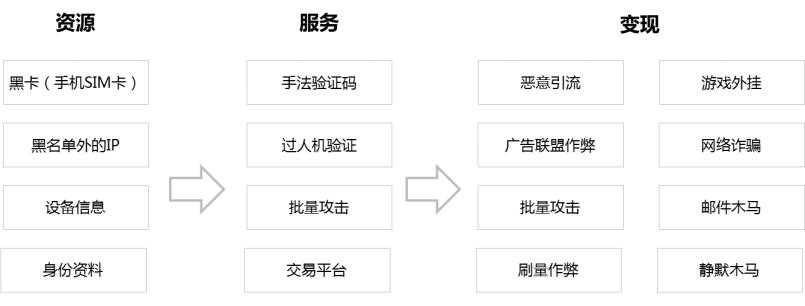
Figure 1 Composition of the industrial chain of "black and gray production"
Second, "black and gray production" has formed a professional and technical operation mode
In recent years, the "black and gray production" evil technology has undergone major changes, and has developed from virtual machines and group control to the current "group control + manual brush volume".
Stage 1: The virtual machine stage, which is the initial stage of the "wool party" industry. The black production of "Silk Wool" belongs to an organized industrial chain, some people provide mobile phones and accounts, some people provide automated tool platforms, and some people are responsible for brushing volume.
Stage 2: Group control stage. By purchasing cheap mobile phones or second-hand mobile phones to form a "mobile phone wall", using the machine modification tool to modify the mobile phone model, MAC address, IMEI code (mobile phone serial code), GPS positioning and other equipment information, so as to continuously forge new devices. There are also ways to complete clicks, APP downloads, and activation accounts and applications by using customized ROMs, manipulating mobile phones through group control software, and imitating real people to automatically complete operations.
Stage 3: "Group Control + Artificial Stage". At this stage, the "wool party" evolved into the "human flesh wool party" and the "real wool party" (real crowdsourcing). Organizers publish project tasks on the live-action crowdsourcing software and platform, such as users clicking on the project to earn points, points can be exchanged for red envelopes, etc., so as to attract real people to participate in the activity.
According to statistics, at present, the malicious registration attacks launched by "black and gray production" on the whole network can reach 8 million times per day, and the active fraudulent mobile phone number exceeds 1.5 million per day, with an average of 6 attacks per mobile phone number per day.
According to the "black and gray production" evil methods that have been explored so far, the scenes of "black and gray production" mainly include malicious registration, malicious attacks, and real people crowdsourcing evil.
Scenario one
Take malicious registration as the core resource
With the deepening of the "card breaking action", the previous method of directly registering a large number of APP accounts by purchasing mobile phone cards at will is no longer feasible. The "black and gray production" adopts the form of "roundabout operation" and forms a new process: in the first step, the card merchant purchases the card from the three major operators, virtual operators, and overseas operators, or hijacks the user's mobile phone number through technical means, and raises the card number through the "cat pool"; the second step, the number merchant obtains the mobile phone number and verification code provided by the card merchant through the "code receiving platform" and registers a false account on the APP; the third step, the number party is used to trade with the card dealer, or the false account is obtained through the "card issuing platform", and finally various malicious operations of "black and gray production" are carried out. The specific process of malicious registration is shown in Figure 2.
Figure 2 Malicious registration flowchart
Scenario two
Malicious automation technology is the main attack method
As Internet companies strengthen risk control of APP, risk account libraries, risk IP libraries, and risk device number libraries are established successively, and are interrelated with account usage behaviors, "black and gray production" began to adopt various malicious automation technologies: from the original simple proxy IP pool to dynamic IP; from group control devices to cloud control devices; from using ROOT devices to modify device numbers to customized ROM directly modifying device numbers to hide real IP or device locations and avoid APP risk control.
Under the influence of malicious automation technology, the process of "black and gray production" has also changed: the first step is to carry out dynamic IP conversion through proxy IP pool, second dial IP, IP magic box, overseas IP proxy, etc.; the second step, using SaaS services and dynamic IP technology, build a "second dial machine or VPN channel" on the public cloud, build a wireless device pool such as mobile phone pool and mobile phone module pool, and form a malicious attack device group; the third step, Use group control or cloud control to manipulate and attack APP automation scripts (key wizards or Auto .js), or directly crack the client and server communication protocols, simulate automation scripts, and forge operation content. The specific process of automating a technical attack is shown in Figure 3.
Figure 3 Flowchart of automated technical attacks
Scenario three
Crowdsourcing with real people to circumvent risk control
With the enhancement of the awareness of prevention and control of platforms in many vertical fields, some platforms have introduced regulations on real-name authentication before users receive gift packages when they are acquired, so as to prevent malicious attacks by "black production" against the welfare of new users. This method does avoid the "black and gray production" through the automatic registration of tools to achieve profits, but it also triggers real people cheating or real people crowdsourcing behavior of reselling accounts after real users authenticate. That is, the original through automated robots, now turned to real personal real-name crowdsourcing for profit, its behavior is mixed in the real behavior of individuals, it is not easy to be discovered. At present, the live crowdsourcing model shows a rapid upward trend.
The above is only part of the "black and gray production" scenario, and does not involve "black production" scenarios such as network fraud, network attacks, and computer destruction.
Resolutely fight the "black and gray production" digital and intelligent prevention and control campaign in the communications industry
"Black ash production" has an inseparable relationship with the communication industry. From the perspective of the purpose of evil and the division of labor in the process, "black and gray production" requires a steady stream of low-cost real-name mobile phone cards, IP address pools, and communication resources such as mobile phones, PCs and cloud hosts. In order to maintain a clear space for the network and protect the legitimate rights and interests of the people, the three basic operators should fulfill the obligations of state-owned enterprises and assume social responsibilities.
Considering the complexity of the current "black and ash production", the digital and intelligent prevention and control of the communication industry is not achieved overnight, but it is necessary to deeply study the internal and external roots, take practical measures, and eliminate all illegal acts. In addition, this campaign cannot be promoted unilaterally by operators alone, but requires the participation of competent government departments such as the Cyberspace Administration of China and the Public Prosecutor's Office, as well as Internet enterprises, financial institutions, social organizations, and the masses of the people.
Proceeding from the overall situation and combining the actual situation of operators, this paper puts forward the following suggestions for operators to fight the "black and gray production" digital and intelligent prevention and control campaign in the communications industry.
Recommendation 1
Build an all-round, three-dimensional joint control and defense system
Taking the maintenance of the safety of the people's property as the starting point, we take the initiative to assume social responsibility, take the initiative to participate in the actions of the competent departments, and build a joint prevention and control system of "civil air defense + technical defense".
In terms of civil air defense, we should establish correct corporate values within the enterprise, strengthen the supervision of internal personnel and partners, eliminate all illegal risks, and put an end to low-quality and ineffective development.
In terms of technical defense, on the basis of the digital transformation of state-owned enterprises, strengthen investment and research and development in the digitalization of risk control, solve technical blind spots and difficulties, and improve technical prevention capabilities.
In terms of joint prevention and control, in accordance with the division of labor in the "black and ash production" industrial chain, the competent departments will take the lead in building a prevention and control system for major industries and enterprises, and on the basis of ensuring national security, data security and personal privacy security, digital technology will be used to monitor key information such as risk accounts, mobile phone numbers, IP addresses, equipment numbers, bank accounts and attack types, and comprehensively improve the efficiency of prevention and control.
Recommendation two
Implement a digital and intelligent prevention and control system, and use technical countermeasures to build a "black ash production" prevention and control ecosystem
According to the three major evil scenes of "black and gray production", the communication characteristics of different communication tools in different scenarios can be sorted out, and the four major risk types of "number type, network type, device type, and real person type" can be summarized, as well as behavioral characteristics such as centralized network access, centralized attack, multi-frequency change IP, and centralized device.
The three elements of mobile phone number, APP account number and bank card are especially critical in the malicious attack and defense confrontation of "black and gray production". The "black and gray production" attacker has connected the three major elements together through automation technology; on the defensive side, due to industry segmentation, enterprise competition and other reasons, it is often the competent department that urgently leads the manual traceability after the case occurs, and can only see one block at the fastest speed.
In summary, the author suggests that operators take the initiative to assume heavy responsibilities, take the lead in internally building a digital and intelligent prevention and control system of "technological countermeasure technology", deeply open up system platforms such as operating domains, business domains, and management domains, organize special research, timely introduce the predictive data of security protection agencies for data integration and mining, and implement an automated prevention and control mechanism of one-click penetration to solve the problem that each system platform cannot be automatically docked and cannot be traced back.
Operators can also simultaneously build a data exchange platform with privacy computing as the core in the industry, or provide "black and ash production" prevention and control data services to empower the outside world, conduct real-time interaction and verification of the three major element resources and attack types, carry out early warning prevention and control in advance, sort out the "black and gray production" industrial chain, and build a "black and gray production" prevention and control ecosystem.
Recommendation three
Take the initiative and take precise measures to strengthen the publicity and education of "black and gray production"
The prevention and control of "black and gray production" is inseparable from the understanding and support of the people, and it is necessary to publicize and educate high-risk areas and high-risk user groups, and improve the prevention and control effect through precise policies and early prevention.
On the basis of complying with national laws and regulations and protecting personal privacy and security, operators can, under the guidance and leadership of the competent departments, analyze the risk users on the "black and ash production" chain through big data technology, and carry out point-to-point publicity and education in advance; synchronously strengthen the control of "black and gray production" communications, incorporate the latest requirements of the competent departments into the network access protocol, optimize the network access protocol in real time, and incorporate the "black and gray production" communication risks into the knowledge clause in advance, and popularize publicity and education in advance.
End
Author: China Unicom Quanzhou Branch Huang Qinhong
Editor-in-Charge/Layout: Fan Fan
Review: Shen Qing
Producer: Liu Qicheng
I knew you were "watching"