This article has been updated to include details about the latest Log4j releases, new exploit vectors, and the risks associated with all Java versions.
Just as the majority of racing enthusiasts watch verstappen and Hamilton's F1 championship battle, the majority of Internet companies are being frightened by a sudden incident.
The average user may not notice that Twitter, Facebook, Gmail, and other services we use on a daily basis are not out of business. But just recently, a bug in Log4j's open source technology caused panic in the global information security community.
The bug has affected billions of devices, and companies are scrambling to install fixes, while the open source community is aware of a deeper problem — where to find money to feed volunteers supporting open source projects like Log4j.
Before diving into so many complex topics, let's take a brief look at the background of Log4j technology and security issues.
What is Log4j?
Log4j 2 is an open source Java-based logging framework that is one of the Apache Foundation services that anyone can use for free. Many enterprises are using this logging software to track activity on their servers, even client applications.
For example, when we visit a website, the logger registers our IP address, browser and the pages we visit. With this data that is closely related to activities, businesses can address any issues that arise in their services.
Because the Log4j library is based on Java, the billions of devices supported by the framework could be put at risk by their security vulnerabilities.
What exactly is the bug in Log4j?
The vulnerability, which was last week listed as CVE-2021-44228, could allow an attacker to remotely execute code via specially crafted strings. Due to the extreme popularity of Log4j, cybercriminals can easily manipulate log strings and thus take control of the target server or client.
The main reason for this bug is that some versions of Log4j allow arbitrary text to be executed via the Directory Lookup Protocol (LDAP protocol).
Please note that this #log4j问题正令整个互联网陷入危机. The key to all this is a simple "${jndi:ldap" string #Log4Shell#log4jRCE
⬇️
— Emy | eq (@entropyqueen_) December 11, 2021
According to a recent Bloomberg report, the vulnerability was first reported to Log4j project maintainers on Nov. 24 by a security researcher on Alibaba's team.
Who will be affected?
Honestly, the simpler question would be "Who will it not affect?" "Log4j's open source features, combined with its wide range of compatibility, make it an excellent solution that is actually used by many vendors, including Apple, Microsoft, Steam, Twitter, Baidu, and Cloudflare.
So as soon as the news of the Log4j vulnerability came out, major companies were scrambling to scan servers to check whether they were at risk.
Performing a large-scale scan of multiple hosts using Apache Log4j (Java Logging Library) found that they were indeed vulnerable to remote code execution vulnerabilities (https://t.co/GgksMUlf94).
Please use our API to check "tags=CVE-2021-44228" for the source IP address and other IOCs. #threatintel
— Bad Packets (@bad_packets) December 10, 2021
Programmers have also tested various sites and services to check the potential scope of the attack; interested friends can click here to see the full list.
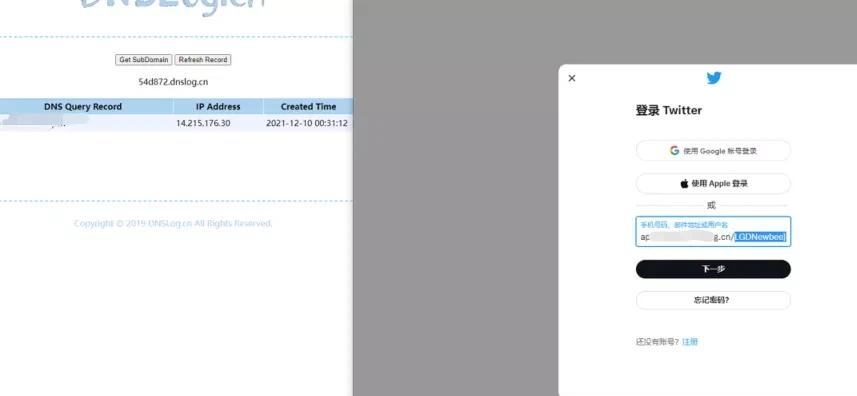
Image: As can be seen from the IP address, Twitter is making extensive use of the Log4j service
The good news is that some media have found that many enterprises have deployed multiple firewalls to defend against cyber attacks. So even though some servers may be affected by Log4j attack activity, other security systems can effectively block the offensive.
This problem was first discovered on the Minecraft site, where researchers have found that passing specific strings to the server, or even through a chat box in the game, can put the system under the control of an attacker. Matthew Prince, CEO of Cloudflare, a network infrastructure vendor, tweeted that the company will provide a series of targeted protection measures to all customers, including those who use the free tier.
We've determined that the #Log4J issue is quite serious, so we'll try to provide at least some level of protection to all @Cloudflare customers by default, including free customers who don't enjoy WAF Firewall services. We are looking at how to safely achieve our conservation goals.
— Matthew Prince (@eastdakota) December 10, 2021
It is worth mentioning that Log4j may even affect some smart devices running Java server components. So everyone's smart toaster may also be the target of hacking attacks... Although it doesn't seem to make much sense.
Data security platform LunaSec also provided a solid technical explanation of the potential impact of the vulnerability in an official blog post.
Finally, let's use a tweet to summarize how widely Log4j is used.
Have you heard of the Witty rover that landed on Mars in 2020? It is also powered by Apache Log4j.
https://t.co/gV0uyE1ylk#Apache#OpenSource#innovation#community#logging#servicespic.twitter.com/aFX9JdquP1
— Apache – The ASF (@TheASF) June 4, 2021
What are the mitigations?
Just hours after the bug was exposed, the Apache Foundation's security team released a new log4j version (v15.0) with patches to protect the system from attacks.
Minecraft developer Mojang Studios has also released a guide to help users running official game clients and game servers quickly fix bugs. The guidelines also warn that other users running third-party game clients may have to wait for the appropriate vendor to release a fix. In addition, the Swiss government's Computer Response Group (CERT) has also published easy-to-understand prevention guidelines on Twitter in the form of pictures.
Please note: We found a large number of scans for #log4j vulnerabilities and decided to publish this blog post with guidance: https://t.co/dtEXfY1G16
Please install the patch now! pic.twitter.com/HSedlSed0V
— GovCERT.ch( @GovCERT_CH) December 12, 2021
Vendors such as Red Hat and VMWare have also released their own bug fixes. Dear server administrators, please click here to refer to several server security blog posts for detailed mitigation strategies. A GitHub user also produced a very useful list of patches released by several vendors, including Netflix, Citrix, Docker, and Oracle.
Apache has also released version 2.16.0 of the Log4j framework, which completely removes the mail lookup function to eliminate security threats. In addition, the new version disables the automatic parsing of lookup information contained in a pointer message or its parameters.
It's just getting started
While service providers and the open source community are working around the clock to solve problems and try to protect as much as possible all systems that use Log4j, the real threat still hangs above our heads.
According to a report released by Blending Computer last night, attackers are exploiting this vulnerability to install cryptocurrency mining software, malware, and deploy a massive DDoS (distributed denial of service) botnet. Microsoft's threat intelligence team has also noticed that many attackers are using the Colbat Strike penetration detection tool to carry out credential theft.
Sean Gallagher, a senior research researcher at Sophos, also said that the security vendor has detected a large number of remote code execution attempts:
Since December 9, Sophos has detected hundreds of thousands of remote code execution attempts using the Log4Shell vulnerability. Initial attempts came from proof-of-concept (PoC) exploit testing performed by security researchers and potential attackers, plus self-detecting online vulnerability scans. After this, the attackers began trying to install mining programs, including the Kinsing miner botnet.
The latest intelligence also suggests that attackers are trying to exploit this vulnerability to steal keys used in Amazon Cloud Technology (AWS) accounts.
Security researcher Greg Linares said in a tweet that a malicious attacker could be building a worm that could be used to attack a large number of servers through the Log4j vulnerability, causing damage or demanding ransom.
#Log4J As far as I can see, there is evidence that a worm program specifically targeting this vulnerability will appear in the next 24 to 48 hours.
The virus is able to spread itself and set up self-hosted servers on the infected endpoint.
In addition to manufacturing flow and leak files, it will also have c2c capabilities.
— Greg Linares (@Laughing_Mantis) December 12, 2021
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) also issued a warning, noting that the vulnerability "is being exploited by an increasingly wide range of malicious attackers; given the breadth of the impact, the cyber defense side is facing urgent challenges." The bureau recommends that organizations disable all external-facing devices running Log4j and set rules based on vulnerability-related characteristics to enhance the security level of existing firewalls.
Security researchers discovered last night that the Log4j bug affects all Java versions. So even if you're running Java, you still need to install additional Log4j fixes.
Support for LDAP serialization payloads has just been added in JNDI-Exploit-Kit. So as long as the classes used in the serialization payload are in the application's classpath, then this vulnerability will affect the *everything* java version. Don't think that using the latest version of Java is safe and worry-free, please update your log4j as soon as possible! pic.twitter.com/z3B2UolisR
— Márcio Almeida (@marcioalm) December 13, 2021
A report on The Verge notes that if researchers change the device name to a specific string that could exploit the vulnerability, ping access can be obtained from servers like Apple and Tesla.
The issue of underpayment of contributors to the open source community has caused public outrage
The Discovery of the Log4j bug once again shows that large enterprises around the world are relying heavily on free and open source software. There's nothing inherently wrong with this dependency, but the problem of underpaying contributors to the open source community has caused outrage.
Google cryptographer Filippo Valsorda mentioned on his personal blog that part-time maintainers who fixed the Log4j bug contributed greatly to the project, but that only three sponsors of the project on GitHub were willing to pay the project volunteers.
He also noted that contributors can only get a small return on their money through GitHub or Patreon, but their developments often underpin multimillion-dollar businesses. In addition, bugs in these important systems are likely to overwhelm the entire Internet in an instant, and there is no reason why we should ask too much for these civilian heroes who just take their spare time to contribute almost free of charge.
These maintainers are fixing serious vulnerabilities that could cost millions of dollars (or even orders of magnitude higher).
"I spend my spare time studying Log4j."
"I've always dreamed of working full-time in open source."
"There are three sponsors who are funding the work of @rgoers: Michael, Glenn and Matt."
Guys, what are we doing... pic.twitter.com/2hAxUWCjuC
— Filippo ${jndi:ldap://filippo.io/x} Valsorda (@FiloSottile) December 10, 2021
Matthew Green, a professor of cryptography at Johns Hopkins University, believes that the open source industry needs a truly extensive list of open source libraries and technologies so that more people can participate in these projects that are extremely important to the smooth operation of the Internet.
Well, I want to emphasize that if people want to solve this problem, the most urgent resource may not be money. "Visibility" is even more important. We all know there's a problem, but we don't know exactly where the problem is.
— Matthew Green (@matthew_d_green) December 11, 2021
Dan Lorenc, founder of security vendor Chainguard, said that while companies are willing to fund open source projects, it is difficult to find the right key projects, especially the project maintainers themselves. Ideally, he also mentioned, the industry could directly fund teams responsible for maintaining three or four projects.
This may sound unrealistic, but the real conundrum is how to distribute, not how to raise money. After all, the Internet industry is notoriously rich.
Companies have budgets and are willing to spend money, but they are particularly short of time. Unfortunately, finding projects that really need help, especially open source maintainers who are willing to trade their energy and investment for money, is the real challenge. pic.twitter.com/mFkOoOVYXn
— Dan Lorenc (@lorenc_dan) December 12, 2021
Contributors say they are paid very little for open source contributions, and that the job alone will barely make ends meet. Such a situation can only be described as sad.
Hopefully, this question will eventually awaken the industry to this group of open source contributors who have spontaneously banded together and are willing to work to keep the Internet running. I hope that this thunderstorm will not just stir up a ripple, and will not stop at people's verbal discussions.
Finally, let's conclude the event with an XKCD comic.