IT House February 22 news, Trellix Advanced Research Center today released a blog post, disclosing the privilege execution vulnerability in iOS and macOS systems, attackers can exploit the vulnerability to obtain iPhone and Mac users' messages, location data, photos, call logs, etc.
Trellix discovered the first vulnerability in the coreduetd process, which could allow an attacker to access an individual's calendar, address book, and photos.
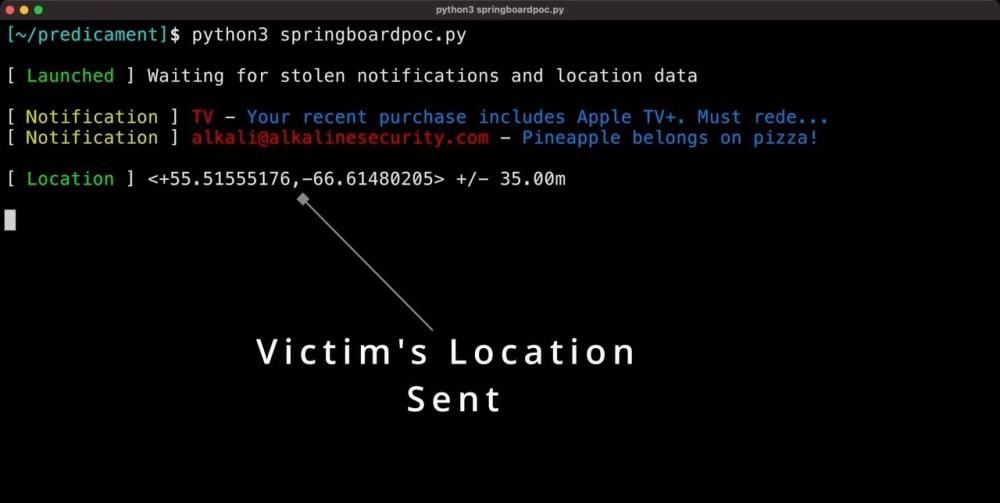
In addition, attackers can also exploit vulnerabilities in OSLogService and NSPredicate in Springboard to gain access to cameras, microphones, call logs, etc.
Trellix has reported the vulnerability to Apple. Apple has fixed two vulnerabilities, CVE-2023-23530 and CVE-2023-23531, in iOS 16.3 and macOS 13.2 Ventura.
Trellix recognized Apple's repair speed in a blog post, and subsequent measurements found that Apple had indeed fixed the above vulnerabilities by improving the memory handling mechanism.
Trellix Advanced Research Center Discovers a New Privilege Escalation Bug Class on macOS and iOS