【Jiaqin Comment】The chip protection method patent of Xinchi Technology not only avoids the leakage of information in the chip by running the chip in the first security mode, but also greatly increases the time and cost of a large number of consecutive attack attempts, and the difficulty of the attack is increased, which greatly improves the security of the chip.
Jiwei Network News, recently, the 2021 Fifth Senior Engineer Intelligent Automobile Annual Conference and Golden Globe Award Ceremony with the theme of "Breakthrough and Reconstruction" was held in Shanghai. With its outstanding market performance, Chip Technology won three awards, including the annual intelligent driving chip high-growth supplier and the annual intelligent gateway chip high-growth supplier.
Usually, the chip will have a variety of protection and attack detection circuits, which can detect and detect attacks, and respond in time such as reset restart, so as to avoid hazards such as sensitive data leakage. In this way, to successfully crack the chip, it will take several different attempts and adjust the attack parameters to be effective. Although the chip can be reset and restarted immediately when an attack is detected, it is impossible to avoid the attacker's long-term large-scale attack attempts of different types, and with the upgrading of attack methods and the advancement of attack technology, the security of the chip is constantly challenged.
To this end, on May 9, 2020, Chip Company applied for an invention patent entitled "Chip Protection Method, Device, Storage Medium and Vehicle Chip" (Application Number: 202010384943.4), and the applicant was Nanjing Chip Chi Semiconductor Technology Co., Ltd.
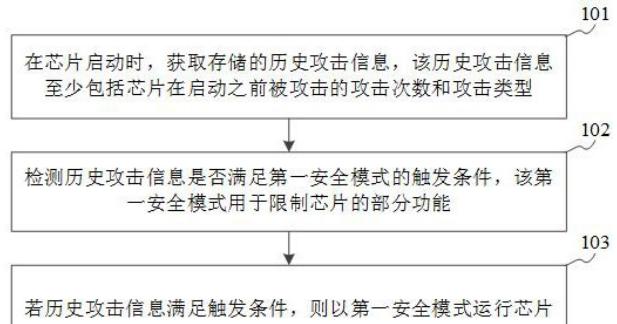
Figure 1 Flowchart of chip protection method
FIG 1 is a flowchart of the chip protection method proposed in the present invention, the method mainly comprises the following steps: First, when the chip is started, the stored historical attack information is obtained, the historical attack information includes at least the number of attacks and attack types (101) of the chip before starting. Historical attack information is the information related to the attack recorded before the chip is started, the information includes at least the number of attacks and the type of attack, may also include the time of the attack, the user identity information at the time of the attack, the location where the attack occurred at least one of the. Attacks on chips can be divided into logical attacks and physical attacks, logical attacks use logical vulnerabilities in chips to attack, try to obtain sensitive data, disrupt or obtain system control permissions, etc., also known as illegal access attacks; physical attacks are the use of physical means to attack chips.
Then, detect whether the historical attack information satisfies the trigger conditions of the first security mode, which is used to limit part of the function of the chip (102). The first safe mode is the operation mode that limits some functions of the chip to improve the security of the chip. When the chip is an in-vehicle chip, the first safety mode can retain the most basic functions that can ensure the normal operation of the vehicle, while restricting the use of other functions. For example, the first security mode can disable access to sensitive information, or destroy sensitive information from chips to avoid the leakage of sensitive information after further attacks. When the historical attack information satisfies the trigger condition, step 103 is performed; when the historical attack information does not meet the trigger condition, the chip may be run in normal mode.
Finally, if the historical attack information satisfies the trigger condition, the chip (103) is run in the first safe mode. In summary, when the chip is started, the stored historical attack information can be obtained, and after that, it can be detected whether the historical attack information meets the trigger conditions of the first security mode, and if so, the chip is run in the first security mode.
In short, the chip protection method patent of Chip Chi Technology limits some functions of the chip by running the chip in the first security mode, which not only avoids the information in the chip from being leaked, but also greatly increases the time and cost of successive attack attempts, and the difficulty of attack is increased, which greatly improves the security of the chip.
As a representative of the field of independent automotive chip, Xinchi Technology accurately grasps market opportunities with excellent product strength. In the future, Xinchi Technology will continue to play a good role as the supporter of the underlying hardware, provide a solid vehicle-grade hardware foundation for "software-defined vehicles", and serve the global automotive industry with high-performance and highly reliable "China Core".
About Jiaqin
Shenzhen Jiaqin Intellectual Property Agency Co., Ltd. is composed of intellectual property experts, lawyers and patent agents who have worked in Huawei and other Fortune 500 companies for many years, is familiar with the legal theories and practices of intellectual property rights in China and Europe and the United States, and has rich experience in global intellectual property application, layout, litigation, licensing negotiation, transaction, operation, standard patent co-creation, patent pool construction, exhibition intellectual property, cross-border e-commerce intellectual property, and intellectual property customs protection.
(Proofreading/Holly)