Recently, the news about Zhihu layoffs flowed out on the Internet, and then some netizens pointed out that Zhihu installed a "behavior perception system" that can monitor employees' Online behavior to analyze whether employees have a tendency to leave. Zhihu responded that it had never installed and used the network transmission behavior perception system, and would not enable similar software tools in the future.
The incident sparked a discussion about the adoption of software by enterprises to manage employee network behavior.
For what purposes do companies use such software and how do they use it? Is it an invasion of employee privacy? On February 15, The Paper (www.thepaper.cn) interviewed network information security experts, lawyers, and scientific and technological ethics scholars to answer questions.
Pictures of the monitoring system on the Internet
According to a practitioner in the network security industry, companies use such "online behavior management" software to worry about the leakage of corporate data to deter employees. He bluntly said that such software would invade the personal privacy of employees.
Some lawyers said that for management purposes, employers can use this kind of management software to a limited extent without the knowledge of employees, and if they invade the private sphere of employees, it is an infringement.
At the same time, this real-time, all-round monitoring model has raised concerns among scholars concerned about the ethics of science and technology, between the basic rights of people as subjects and the rights and interests of the collective, where should privacy be biased? How should the use of such technologies be regulated when such technologies have been widely used?
In 2020, network security business revenue accounted for 61.35% of revenue. Screenshot of the 2020 Conviction Service Annual Report
The network knows to monitor the tendency of employees to leave, and knows to deny
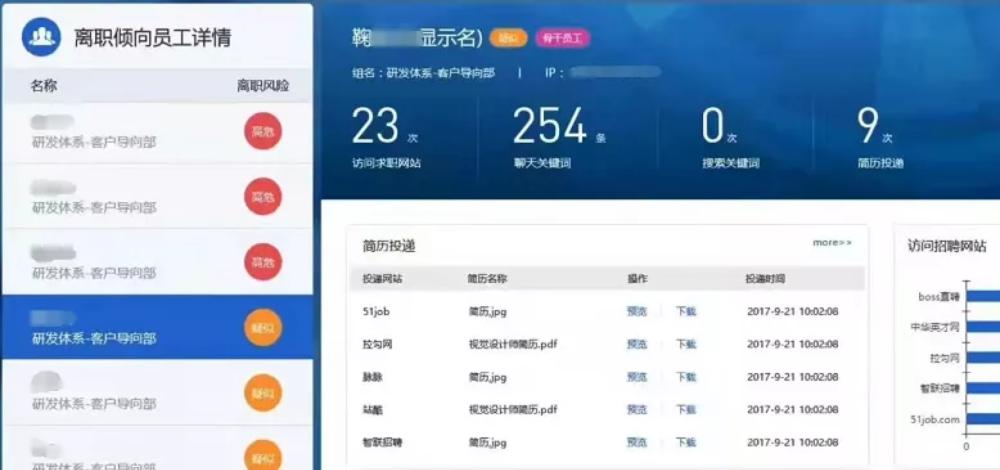
A system background picture uploaded online shows that an employee surnamed Ju visited the job search website 23 times, submitted his resume 9 times, and had 254 chat records containing keywords. Some netizens said that Zhihu installed a behavior perception system to monitor employees' Internet access, learned that they browsed recruitment websites, submitted resumes and other behaviors, in order to analyze whether employees have a tendency to leave.
Subsequently, Zhihu denied the installation of a "monitoring employee behavior perception system". A staff member of Zhihu told the surging news on the afternoon of February 14 that after verification, it was found that the source of the incident was that netizens posted a screenshot of a software system suspected of monitoring the departure of employees on the Internet, and was misinterpreted and associated with Zhihu by some people.
The staff member said: "We declare that We have never installed and used the behavior perception system mentioned on the Internet, and we will not enable similar software tools in the future." For screenshots of the system online, we have never been exposed to it, so it is not clear how authentic it is. ”
"In particular, it is necessary to state that the illegal collection of personal information security is itself a serious deviation from the values of Zhihu, and we have always been firmly opposed to such systems." The staff stressed.
The aforementioned behavior perception system is alleged to have been developed by the listed company Deeply Believe Service Technology Co., Ltd. (hereinafter referred to as "DeepLy believe service"). According to the company's official website, Convinced Service was founded in 2000, and according to the annual report released by Convinced Service in 2020, its network security business revenue was 3.349 billion yuan, accounting for 61.35% of the total revenue.
The Paper noted that the official website of The Paper has introduced a product called "Internet Behavior Management", which includes Internet behavior audit, illegal Internet behavior control, enterprise information leakage prevention, Internet traffic control, and work efficiency analysis. Among them, the work efficiency analysis function is introduced, which can intelligently analyze and predict work efficiency based on the dynamics of Internet behavior, which is convenient for enterprises to take timely measures to reduce losses.
Industry insiders: Mainly used to improve work efficiency and protect information security
With the fermentation of public opinion, such technologies and products that monitor the online behavior of enterprise employees have entered the public eye, triggering discussions among netizens, and many people have questioned the risk of leakage of employees' personal privacy. For what purposes are such technologies used? How does the product work? And to what extent is it used?
Li Shaopeng, founder of The World Consulting and an expert of the China Cyberspace Security Association, told The Paper that around 2000, with instant messaging software such as QQ and MSN, software that manages employees' Online behavior has become popular. He said that such network-wide behavior management products were originally called SWG (web security gateways) abroad, mainly to prevent employees from bringing viruses to the Internet and causing external intrusions, while in China it has become Online behavior management.
The product introduction page of the official website of the service
According to Li Shaopeng's understanding, the use of Internet behavior management software is mainly within private enterprises, and the situation of public institutions and state units is relatively rare. He explained that some companies do not want employees to do things that are not related to work during working hours, and are worried that employees will use such behavior management software to monitor employees' network behavior during working hours, such as chatting, posting, shopping, watching videos, etc. during working hours.
But in Li Shaopeng's view, "the operation and maintenance management model (adopted by enterprises) is very normal." Li Shaopeng said that companies that use such software generally inform employees in advance, and the purpose is mainly to deter employees. Of course, there are a few cases where companies do not inform employees, but directly monitor the behavior of employees and then take measures.
For the operation mechanism of Internet behavior management products, Li Shaopeng introduced that as long as employees are online, network traffic will be generated. Set up some detected keywords, protocols, specific websites, etc. for traffic to find out if there is a place related to outreach work. For example, if employees often send resumes to recruitment websites, companies can suspect whether employees want to jump ship.
In addition, the information captured by the Internet behavior management product can be set, such as the enterprise set up a fixed listening website, if the employee visits, it will be crawled to send text, email and other browsing records, but third-party communication tools generally can not be crawled. For example, weChat App has its own encryption mechanism.
According to a previous report by Workers Daily, You Jing, who works at a private enterprise in Jinan, Shandong Province, once used an office computer to download game software and was warned by a phone call from the company's technical department. "At that time, the head of the department was holding a video conference, and the technical department warned me that I had occupied the network bandwidth, which affected the video conference, and if it was serious, it would be notified to the personnel department." She said the employee handbook did list "not allowed to do things that are not related to work", but she did not expect to be "caught".
"This is a common traffic distribution management in Internet behavior management." He Zhe worked in product research and development at a leading company that provided online behavior management services for enterprises. He revealed that Internet behavior management products generally include hardware and software, with basic functions such as identity authentication, application permission control, data analysis, and security protection to help enterprises monitor employees' Online behavior, with the purpose of improving work efficiency and protecting information security.
A person familiar with Internet behavior management products also told The Paper that the essence of such products is to prevent the leakage of information within enterprises.
Scholars recommend adhering to ethical norms and protecting employee privacy
"Some people think that the working hours of employees belong to the company, but at any time, people have the basic right to be a free subject." Wen Xianqing, an associate professor at the Institute of Artificial Intelligence Ethics Decision-making at Hunan Normal University, believes that from the perspective of scientific and technological ethics, it is inappropriate to conduct all-round real-time monitoring of employees' work.
He pointed out that compared with traditional business management behaviors (such as clocking in to work), software monitoring is real-time and covers the whole process. In this way, the space for interpreting the behavior of a certain point in time becomes larger, and it will become a monitoring of employees as a subject of rights, undermining their basic freedoms and rights as personalities. For example, is an occasional cup of coffee likely to be evidence of negative slacking off? ”
The question that should be discussed in the topic, he argued, was where people placed privacy and attached it to other rights, such as the safety or effectiveness of collectives or enterprises, or to the fundamental rights of individuals.
He proposed that online behavior monitoring is not only a matter of enterprise management, but also involves the basic personal rights of employees, whether the rights of enterprises and employees are reciprocal, and so on. "With such software already widely used, we have to retreat to the second place and require it to comply with some technical ethics norms, such as informing employees of the existence of monitoring and the use of data used by enterprises." Wen Xianqing said.
For the future use of such technologies, Wen Xianqing believes that from the national level, it is necessary to respect the right to freedom, privacy and security of employees as a person from the perspective of basic human rights, and to stipulate the scope of their authority when the industry and enterprises formulate monitoring policies and systems. Second, if technical tools are used to monitor employee behavior, legislation should guide companies to formulate a set of rules that clearly stipulate the collection, dissemination, preservation, and deletion of employee data. Finally, the company itself should have a department to deal with the relevant matters.
Xie Xiaoyun, deputy dean and professor of the School of Management of Zhejiang University, previously said in an interview with Workers Daily that many studies have proved that digital monitoring systems will damage employees' work initiative, reduce employee satisfaction with their work, and trigger negative emotional experiences. He suggested that when designing assessment indicators for digital management, enterprises should pay more attention to ethics and morality, pay attention to protecting the privacy of employees, and avoid the negative effects of digital management.
Businesses using online behavior management products are not without legal risks. Ding Jinkun, a lawyer at Shanghai Dabang Law Firm, said that according to article 1032 of the Civil Code, no organization or individual may infringe on the privacy rights of others by means of spying, intrusion, leakage, disclosure, etc.
Ding Jinkun said that for management purposes, employers can use this kind of management software to a limited extent with the knowledge of employees to prevent employees from deserting or leaking company secrets. The software can generally only be used for business purposes, within a limited range of use, can not invade the private domain of employees, otherwise it is infringement and must bear legal responsibility. Employers are obliged to protect the privacy and safety of employees, not to infringe upon them. In such cases, the labor inspection department should intervene in the investigation and order the employer to use the software to manage employees reasonably in accordance with the law.
Zhao Liangshan, a senior partner at Shaanxi Hengda Law Firm and a well-known public interest lawyer, also believes that if the company's behavior violates the privacy rights of employees, according to the Civil Code, the enterprise needs to bear civil tort liability to employees, such as stopping the infringement, apologizing, and compensating for losses. Accordingly, employees may file a lawsuit against them in order to safeguard their legitimate rights and interests.