◎ Science and Technology Daily reporter Liu Yan
Any Internet user, anywhere in the world, is at risk of indiscriminate U.S. cyberattacks at all times, including its allies.
On the afternoon of March 22, 360 Government and Enterprise Security Group released a technical report, which for the first time fully disclosed the technical characteristics of the Quantum attack platform, a representative cyber weapon used by the NSA (National Security Agency) against targets in China.
Previously, 360 had disclosed that the NSA had launched more than a decade of cyber attacks against the world, and the mainland was one of the key targets.
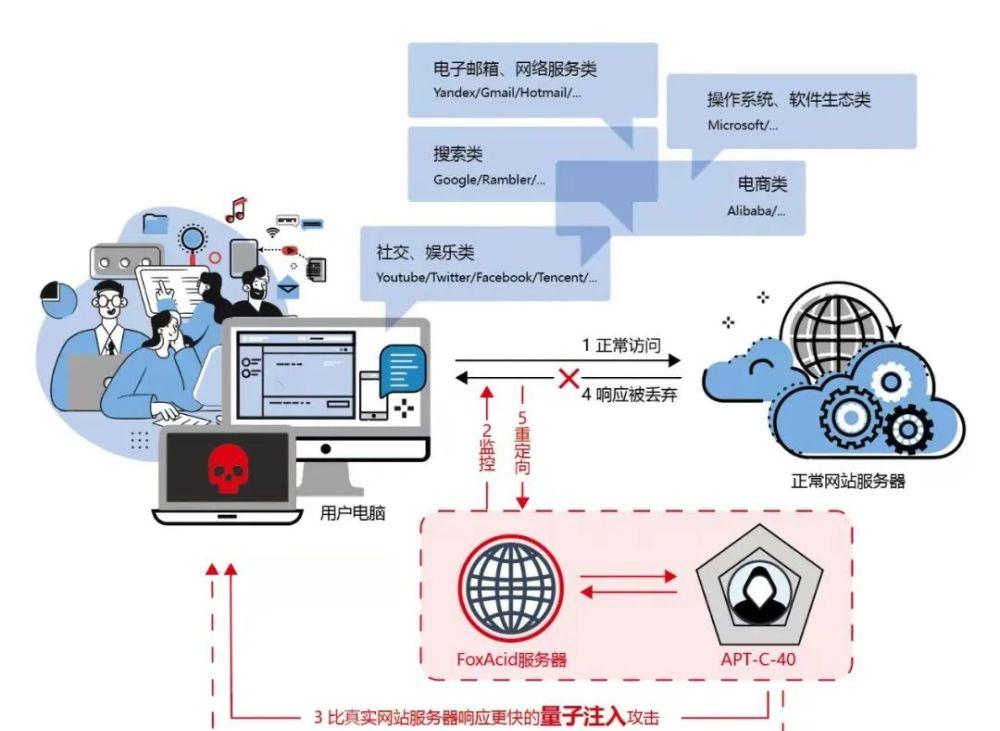
According to the technical report, the NSA uses quantum attack technology to launch a cyber attack against all Internet users around the world who visit US websites such as Facebook, Twitter, YouTube, amazon and so on, and Chinese social software such as QQ is also one of the targets.
Bian Liang, senior security expert of 360 Government and Enterprise Security Group, introduced that quantum attacks are advanced network traffic hijacking attack technologies specially designed by the NSA for the national Internet, mainly for intermediate hijacking of national network communications to implement a series of complex network attacks such as vulnerability exploitation, communication manipulation, and intelligence theft.
The Quantum Attack Platform is the N.S.A.'s most powerful Internet attack tool and one of its most important capability platforms for conducting cyber intelligence warfare, dating back to 2005. Containing multiple sub-projects that begin with QUANTUM, 360 Cloud Security Brain has now discovered nine attack capability modules.
Bian Liang told the Science and Technology Daily reporter: "These 9 types of network attack capability modules have their own emphases, such as quantum injection is mainly used by the NSA to hijack the normal web browsing traffic of Internet users around the world, quantum puppets can provide the attack ability to remotely control any botnet in cyberspace, and quantum phantoms can provide the use of network link intermediate node hijacking technology to achieve the attack ability hidden by attack sources." These functional modules work together to form a highly engineered, automated cyber weapon system. ”
Bian Liang emphasized: "Quantum attacks are targeted attacks against specific targets, extremely hidden, difficult to trace, but can be found, preventable, and broken. For example, the 360 Government and Enterprise Security Group Digital Security Capability System with national APT advanced threat detection and defense capabilities can improve the ability to 'see' and 'respond' to advanced threats. ”
It is understood that in order to monitor global Internet targets, the NSA has formulated a number of operational plans, the specific tasks involved in the relevant plans are implemented through the quantum attack platform, and the entire implementation of the attack has been engineered, automated and artificially artificial.
The list of high-end NSA cyber hacking weapons that have been publicly exposed is numerous, and the quantum attack system is only the tip of the iceberg. In order to grasp the dominance of cyber warfare, the United States is making full use of all advanced technologies and network resources to incorporate a large number of top technical means, high-end talents, and intelligence forces such as quantum attack platforms into the combat sequence, bringing huge hidden dangers to global network security.
In this indiscriminate attack, no country is immune, and few Internet users are immune.
The N.S.A. launched various cyberattacks against the mainland involve many fields, and national security, public safety, and citizens' personal information security are all threatened to varying degrees.
How to deal with this global indiscriminate attack?
Bian Liang suggested that the awareness of network security and confidentiality among the personnel of the organization should be effectively improved, and the security awareness and related decision-making of the leaders should be the top priority of the cyber security fortifications. When a destructive cyberattack is inevitable, resources should be focused on systems that support critical business functions, and even partially affected business systems should be cut down and discarded if necessary.
Bian Liang said: "Network attacks can occur at any time, it is necessary to confirm that the entire information network of the organization has anti-virus and anti-malware protection, and update these tools in a timely manner, while improving the response ability when suffering from network attacks, ensuring that backups are isolated from the network, and ensuring that critical data can be quickly recovered." If industrial control systems or operating techniques are used, manual control testing is required to ensure that the network can still function properly once it is no longer in use. ”
Source: Science and Technology Daily Image from 360 Company
Editor: Liu Yiyang
Review: Wang Xiaolong
Final Judgement: Wang Yu