Well-known cloud service providers are vulnerable to exploitation because using trusted core services can turn a single vulnerability into a global attack.
Attack chain for AWS Glue vulnerabilities
In an analysis released jan. 13, cloud security firm Orca Security said AWS has plugged two vulnerabilities in its core services, one of which could give any user access to and control of any company's infrastructure.
While both vulnerabilities have now been fixed, the entire chain of attacks —infecting core services, elevating privileges, and using that privilege against other users— isn't limited to Amazon. Yoav Alon, chief technology officer at Orca Security, said this approach affects many other cloud vendors. He said that the core of the problem is the lack of isolation between services, and the permissions of different services and users are not refined enough.
The company has already reported similar issues to other cloud services, but Alon won't disclose details about these vulnerabilities unless its disclosure process is in place.
"We see these as the next wave of serious vulnerabilities because the objects of our trust have moved from data centers to cloud services — which is a good thing because cloud service providers are better at security than most companies," he said. Now, the cloud service provider's problem affects you, and you may not even know it. ”
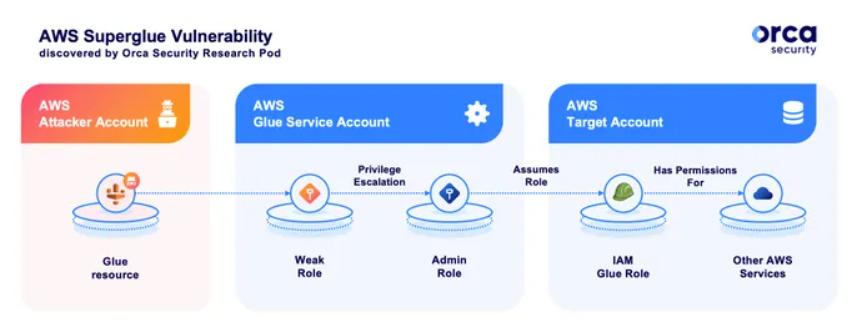
The most serious of the two vulnerabilities is in AWS Glue, a Serverless integration service that allows AWS users to manage, cleanse, and transform data, and make the data store available to users for use by other services. Exploiting this vulnerability, an attacker could infect the service and become an administrator, and since the Glue service is trusted, the attacker could use its role to access other users' environments.
Orca stated in the announcement that the vulnerability allows the company's researchers to "upgrade permissions within the account, which in turn gives unrestricted access to all resources of the service in the service area, including full administrative privileges." ”
Orca's researchers could take on roles in other AWS customer accounts that have a trusting relationship with the Glue service. Orca insists that every account that uses the Glue service has at least one role that trusts the Glue service.
Another vulnerability in the CloudFormation (CF) service allows users to provision resources and cloud assets, allowing researchers to break into CF servers to run as AWS infrastructure services. Orca Security said in the second announcement that the vulnerability is an XML External Entity (XXE) issue that could allow an attack to break through protections that isolate different AWS users.
An AWS representative said in a statement: "We are aware of issues related to AWS Glue ETL and AWS CloudFormation and can confirm that no AWS customer accounts or data have been affected." Upon learning of this from Orca Security, we immediately took action within hours to address the issue and added additional controls to the service to prevent recurrence. ”
Orca's Alon said cloud providers should work to improve the isolation of services to prevent attackers from exploiting vulnerabilities in core services to compromise the security model of the entire cloud. A similar issue affected Azure in August 2021, when researchers at cloud security firm Wiz.io discovered a flaw in the way Microsoft integrated data science feature Jupyter Notebooks with its Cosmo DB database-as-a-service approach. If Jupyter Notebooks is used, an attacker can access another user's Instance of Cosmo DB.
AWS vulnerabilities highlight the pros and cons of the cloud model. Security issues affecting cloud providers often put every customer at risk, with most customers virtually powerless to protect their data and environment. Compare that to a wide range of software issues, such as the Log4j vulnerability: security and IT teams can patch problems, monitor attacks, and take workarounds.
However, eliminating the Log4j problem is still problematic, as different companies patch differently. Orca found that two weeks after the issue was disclosed, three-quarters of customers were still vulnerable to the Log4j vulnerability. On the other hand, Amazon fixed the Glue vulnerability found by Orca within 48 hours and cloudFormation within 6 days, according to the security company.
"Cloud providers are doing a great job of security, but there are still problems," Alon said. If they are better isolated and create a better permissions system in the service, many of these problems can be prevented. If there is a problem with their service, they also need to better isolate their network and have a better security model. ”
Orca Security found the problem in September and October last year. They used fake accounts to test vulnerabilities and prevent researchers from leaking data from other AWS customers. Amazon has fixed the vulnerability and the patch has been tested by Orca to ensure that the patch is actually effective.