CAS 5.3.1系列之自定義Shiro認證政策(四)
CAS官方文檔是介紹基于配置實作shiro認證的,可以參考官方文檔,不過我們也可以通過自定義認證政策的方式實作jdbc認證,pom先加入相關jar
<!-- Custom Authentication -->
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-core-authentication-api</artifactId>
<version>${cas.version}</version>
</dependency>
<!-- Custom Configuration -->
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-core-configuration-api</artifactId>
<version>${cas.version}</version>
</dependency>
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-generic</artifactId>
<version>${cas.version}</version>
</dependency> 如果要用公網提供的基于配置實作的,需要加入:
<!-- Shiro Authentication -->
<dependency>
<groupId>org.apereo.cas</groupId>
<artifactId>cas-server-support-shiro-authentication</artifactId>
<version>${cas.version}</version>
</dependency> 要自定義shiroRealm的,加入shiro相關jar:
<dependency>
<groupId>org.apache.shiro</groupId>
<artifactId>shiro-spring</artifactId>
<version>1.4.0</version>
</dependency> 實作一個Shiro Realm類,僅供參考:
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.*;
import org.apache.shiro.authz.AuthorizationInfo;
import org.apache.shiro.authz.SimpleAuthorizationInfo;
import org.apache.shiro.realm.AuthorizingRealm;
import org.apache.shiro.session.Session;
import org.apache.shiro.subject.PrincipalCollection;
import org.apache.shiro.subject.Subject;
import org.muses.jeeplatform.cas.user.model.User;
import org.muses.jeeplatform.cas.user.service.UserService;
import org.slf4j.Logger;
import org.slf4j.LoggerFactory;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.jdbc.core.BeanPropertyRowMapper;
import org.springframework.jdbc.core.JdbcTemplate;
import org.springframework.jdbc.datasource.DriverManagerDataSource;
/**
* <pre>
*
* </pre>
*
* <pre>
* @author mazq
* 修改記錄
* 修改後版本: 修改人: 修改日期: 2020/04/26 11:33 修改内容:
* </pre>
*/
public class ShiroAuthorizingRealm extends AuthorizingRealm {
Logger LOG = LoggerFactory.getLogger(ShiroAuthorizingRealm.class);
/**注解引入業務類**/
//@Autowired
//UserService userService;
/**
* 登入資訊和使用者驗證資訊驗證(non-Javadoc)
* @see org.apache.shiro.realm.AuthenticatingRealm#doGetAuthenticationInfo(AuthenticationToken)
*/
@Override
protected AuthenticationInfo doGetAuthenticationInfo(AuthenticationToken token) throws AuthenticationException {
String username = (String)token.getPrincipal(); //得到使用者名
String password = new String((char[])token.getCredentials()); //得到密碼
LOG.info("Shiro doGetAuthenticationInfo>> username:{},password:{}",username,password);
//User user = userService.findByUsername(username);
// JDBC模闆依賴于連接配接池來獲得資料的連接配接,是以必須先要構造連接配接池
DriverManagerDataSource dataSource = new DriverManagerDataSource();
dataSource.setDriverClassName("com.mysql.jdbc.Driver");
dataSource.setUrl("jdbc:mysql://192.168.0.152:33306/jeeplatform");
dataSource.setUsername("root");
dataSource.setPassword("minstone");
// 建立JDBC模闆
JdbcTemplate jdbcTemplate = new JdbcTemplate();
jdbcTemplate.setDataSource(dataSource);
String sql = "SELECT * FROM sys_user WHERE username = ?";
User user = (User) jdbcTemplate.queryForObject(sql, new Object[]{username}, new BeanPropertyRowMapper(User.class));
Subject subject = getCurrentExecutingSubject();
//擷取Shiro管理的Session
Session session = getShiroSession(subject);
//Shiro添加會話
session.setAttribute("username", username);
session.setAttribute(ShiroConsts.SESSION_USER, user);
/**檢測是否有此使用者 **/
if(user == null){
throw new UnknownAccountException();//沒有找到賬号異常
}
/**檢驗賬号是否被鎖定 **/
if(Boolean.TRUE.equals(user.getLocked())){
throw new LockedAccountException();//抛出賬号鎖定異常
}
/**AuthenticatingRealm使用CredentialsMatcher進行密碼比對**/
if(null != username && null != password){
return new SimpleAuthenticationInfo(username, password, getName());
}else{
return null;
}
}
/**
* 授權查詢回調函數, 進行鑒權但緩存中無使用者的授權資訊時調用,負責在應用程式中決定使用者的通路控制的方法(non-Javadoc)
* @see AuthorizingRealm#doGetAuthorizationInfo(PrincipalCollection)
*/
@Override
protected AuthorizationInfo doGetAuthorizationInfo(PrincipalCollection pc) {
String username = (String)pc.getPrimaryPrincipal();
SimpleAuthorizationInfo authorizationInfo = new SimpleAuthorizationInfo();
// authorizationInfo.setRoles(userService.getRoles(username));
// authorizationInfo.setStringPermissions(userService.getPermissions(username));
System.out.println("Shiro授權");
return authorizationInfo;
}
@Override
public void clearCachedAuthorizationInfo(PrincipalCollection principals) {
super.clearCachedAuthorizationInfo(principals);
}
@Override
public void clearCachedAuthenticationInfo(PrincipalCollection principals) {
super.clearCachedAuthenticationInfo(principals);
}
@Override
public void clearCache(PrincipalCollection principals) {
super.clearCache(principals);
}
protected Subject getCurrentExecutingSubject(){
return SecurityUtils.getSubject();
}
protected Session getShiroSession(Subject subject){
return subject.getSession();
}
}
自定義授權handler類實作AbstractUsernamePasswordAuthenticationHandler抽象類:
package org.muses.jeeplatform.cas.authentication.handler;
import org.apache.shiro.SecurityUtils;
import org.apache.shiro.authc.*;
import org.apache.shiro.session.Session;
import org.apache.shiro.subject.Subject;
import org.apereo.cas.authentication.*;
import org.apereo.cas.authentication.AuthenticationException;
import org.apereo.cas.authentication.exceptions.AccountDisabledException;
import org.apereo.cas.authentication.handler.support.AbstractPreAndPostProcessingAuthenticationHandler;
import org.apereo.cas.authentication.handler.support.AbstractUsernamePasswordAuthenticationHandler;
import org.apereo.cas.authentication.principal.PrincipalFactory;
import org.apereo.cas.services.ServicesManager;
import javax.security.auth.login.AccountLockedException;
import javax.security.auth.login.AccountNotFoundException;
import javax.security.auth.login.CredentialExpiredException;
import javax.security.auth.login.FailedLoginException;
import java.security.GeneralSecurityException;
/**
* <pre>
*
* </pre>
*
* <pre>
* @author mazq
* 修改記錄
* 修改後版本: 修改人: 修改日期: 2020/04/26 11:03 修改内容:
* </pre>
*/
public class ShiroAuthenticationHandler extends AbstractUsernamePasswordAuthenticationHandler {
public ShiroAuthenticationHandler(String name, ServicesManager servicesManager, PrincipalFactory principalFactory, Integer order) {
super(name, servicesManager, principalFactory, order);
}
@Override
protected AuthenticationHandlerExecutionResult authenticateUsernamePasswordInternal(UsernamePasswordCredential credential, String originalPassword) throws GeneralSecurityException, PreventedException {
try {
UsernamePasswordToken token = new UsernamePasswordToken(credential.getUsername(), credential.getPassword());
if (credential instanceof RememberMeUsernamePasswordCredential) {
token.setRememberMe(RememberMeUsernamePasswordCredential.class.cast(credential).isRememberMe());
}
Subject subject = getCurrentExecutingSubject();
subject.login(token);
//擷取Shiro管理的Session
//Session session = getShiroSession(subject);
final String username = subject.getPrincipal().toString();
return createHandlerResult(credential, this.principalFactory.createPrincipal(username));
} catch (final UnknownAccountException uae) {
throw new AccountNotFoundException(uae.getMessage());
} catch (final IncorrectCredentialsException ice) {
throw new FailedLoginException(ice.getMessage());
} catch (final LockedAccountException | ExcessiveAttemptsException lae) {
throw new AccountLockedException(lae.getMessage());
} catch (final ExpiredCredentialsException eae) {
throw new CredentialExpiredException(eae.getMessage());
} catch (final DisabledAccountException eae) {
throw new AccountDisabledException(eae.getMessage());
} catch (final AuthenticationException e) {
throw new FailedLoginException(e.getMessage());
}
}
protected Subject getCurrentExecutingSubject(){
return SecurityUtils.getSubject();
}
protected Session getShiroSession(Subject subject){
return subject.getSession();
}
@Override
public boolean supports(Credential credential) {
return false;
}
}
同理實作一個Shiro配置類:
package org.muses.jeeplatform.cas.authentication.config;
import org.apache.shiro.mgt.SecurityManager;
import org.apache.shiro.spring.web.ShiroFilterFactoryBean;
import org.apache.shiro.web.mgt.DefaultWebSecurityManager;
import org.apereo.cas.authentication.AuthenticationEventExecutionPlan;
import org.apereo.cas.authentication.AuthenticationEventExecutionPlanConfigurer;
import org.apereo.cas.authentication.AuthenticationHandler;
import org.apereo.cas.authentication.PrePostAuthenticationHandler;
import org.apereo.cas.authentication.principal.DefaultPrincipalFactory;
import org.apereo.cas.configuration.CasConfigurationProperties;
import org.apereo.cas.services.ServicesManager;
import org.muses.jeeplatform.cas.authentication.handler.ShiroAuthenticationHandler;
import org.muses.jeeplatform.cas.authentication.handler.UsernamePasswordAuthenticationHandler;
import org.muses.jeeplatform.cas.authentication.shiro.ShiroAuthorizingRealm;
import org.springframework.beans.factory.annotation.Autowired;
import org.springframework.beans.factory.annotation.Qualifier;
import org.springframework.beans.factory.config.MethodInvokingFactoryBean;
import org.springframework.boot.context.properties.EnableConfigurationProperties;
import org.springframework.context.annotation.Bean;
import org.springframework.context.annotation.Configuration;
import java.util.LinkedHashMap;
import java.util.Map;
/**
* <pre>
*
* </pre>
*
* <pre>
* @author mazq
* 修改記錄
* 修改後版本: 修改人: 修改日期: 2020/04/26 16:35 修改内容:
* </pre>
*/
@Configuration("ShiroAuthenticationConfiguration")
@EnableConfigurationProperties(CasConfigurationProperties.class)
public class ShiroAuthenticationConfiguration implements AuthenticationEventExecutionPlanConfigurer {
@Autowired
private CasConfigurationProperties casProperties;
@Autowired
@Qualifier("servicesManager")
private ServicesManager servicesManager;
//@Bean
public ShiroFilterFactoryBean shirFilter(SecurityManager securityManager) {
ShiroFilterFactoryBean shiroFilterFactoryBean = new ShiroFilterFactoryBean();
shiroFilterFactoryBean.setSecurityManager(securityManager);
//攔截器.
Map<String,String> filterChainDefinitionMap = new LinkedHashMap<>();
// 配置不會被攔截的連結 順序判斷
filterChainDefinitionMap.put("/static/**", "anon");
filterChainDefinitionMap.put("/upload/**", "anon");
filterChainDefinitionMap.put("/plugins/**", "anon");
filterChainDefinitionMap.put("/code", "anon");
filterChainDefinitionMap.put("/login", "anon");
filterChainDefinitionMap.put("/logincheck", "anon");
filterChainDefinitionMap.put("/**", "authc");
shiroFilterFactoryBean.setLoginUrl("/login");
shiroFilterFactoryBean.setSuccessUrl("/index");
shiroFilterFactoryBean.setUnauthorizedUrl("/login");
shiroFilterFactoryBean.setFilterChainDefinitionMap(filterChainDefinitionMap);
return shiroFilterFactoryBean;
}
@Bean
public ShiroAuthorizingRealm shiroAuthorizingRealm(){
ShiroAuthorizingRealm myShiroRealm = new ShiroAuthorizingRealm();
//myShiroRealm.setCachingEnabled(false);
//啟用身份驗證緩存,即緩存AuthenticationInfo資訊,預設false
myShiroRealm.setAuthenticationCachingEnabled(false);
//啟用授權緩存,即緩存AuthorizationInfo資訊,預設false
myShiroRealm.setAuthorizationCachingEnabled(false);
return myShiroRealm;
}
@Bean
public SecurityManager securityManager(){
DefaultWebSecurityManager securityManager = new DefaultWebSecurityManager();
securityManager.setRealm(shiroAuthorizingRealm());
return securityManager;
}
/**
* Spring靜态注入
* @return
*/
@Bean
public MethodInvokingFactoryBean getMethodInvokingFactoryBean(){
MethodInvokingFactoryBean factoryBean = new MethodInvokingFactoryBean();
factoryBean.setStaticMethod("org.apache.shiro.SecurityUtils.setSecurityManager");
factoryBean.setArguments(new Object[]{securityManager()});
return factoryBean;
}
@Bean
public AuthenticationHandler myAuthenticationHandler() {
return new ShiroAuthenticationHandler(ShiroAuthenticationHandler.class.getName(),
servicesManager, new DefaultPrincipalFactory(), 1);
}
@Override
public void configureAuthenticationExecutionPlan(AuthenticationEventExecutionPlan plan) {
plan.registerAuthenticationHandler(myAuthenticationHandler());
}
}
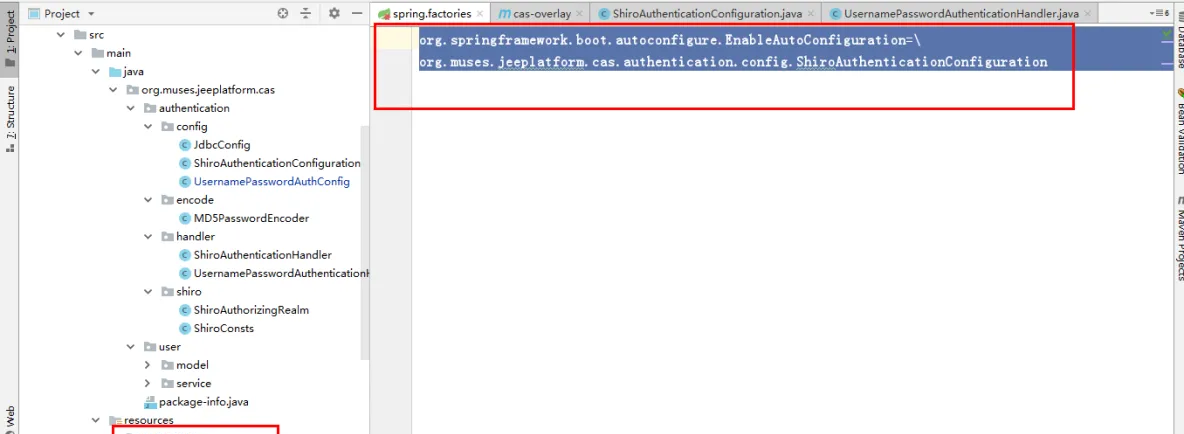
在META-INF檔案夾,新增一個命名為spring.factories的檔案
在這裡插入圖檔描述
org.springframework.boot.autoconfigure.EnableAutoConfiguration=\
org.muses.jeeplatform.cas.authentication.config.ShiroAuthenticationConfiguration
為什麼要這樣做?因為這樣做才能将配置類加載到spring容器,詳情需要跟下源碼,可以參考我部落格:SpringBoot源碼學習系列之自動配置原理簡介
在這裡插入圖檔描述
在這裡插入圖檔描述