最近比較蛋疼。閑的的無聊。。決定做點什麼。什麼簡單做什麼咯!
學習MPLS-×××過程中,提到了IPSEC ×××,決定複習下。
實驗拓撲:
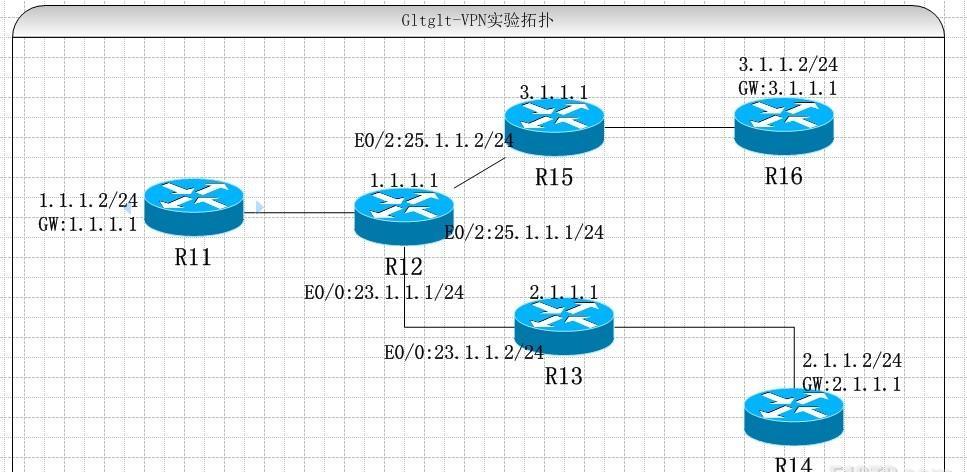
實驗要求:
1、R12和R13之間啟用IPSEC ×××。
2、R12和R15之間啟用IPSEC ×××。
3、R11、R14、R16模拟PC。實驗完成後R11、R14互通,R11、R16互通。
通過PING。引發感興趣流,通過show指令驗證×××的結果。
實驗過程:
R11配置:
R11#show runn
Building configuration...
Current configuration : 1690 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
hostname R11
interface Ethernet0/1
ip address 1.1.1.2 255.255.255.0
ip forward-protocol nd
no ip http server
no ip http secure-server
ip route 0.0.0.0 0.0.0.0 1.1.1.1
R12配置:
R12#show runn
Current configuration : 2523 bytes
hostname R12
!
crypto isakmp policy 10
hash md5
authentication pre-share
crypto isakmp key cisco address 23.1.1.2
crypto isakmp key black address 25.1.1.2
crypto ipsec transform-set cisco esp-des esp-md5-hmac
crypto ipsec transform-set black esp-des esp-md5-hmac
crypto map black 1 ipsec-isakmp
set peer 25.1.1.2
set security-association lifetime seconds 86400
set transform-set black
set pfs group1
match address 120
crypto map cisco 110 ipsec-isakmp
set peer 23.1.1.2
set transform-set cisco
match address 110
!
interface Ethernet0/0
ip address 23.1.1.1 255.255.255.0
crypto map cisco
ip address 1.1.1.1 255.255.255.0
interface Ethernet0/2
ip address 25.1.1.1 255.255.255.0
crypto map black
ip route 2.1.1.0 255.255.255.0 23.1.1.2
ip route 3.1.1.0 255.255.255.0 25.1.1.2
access-list 110 permit ip 1.1.1.0 0.0.0.255 2.1.1.0 0.0.0.255
access-list 120 permit ip 1.1.1.0 0.0.0.255 3.1.1.0 0.0.0.255
R13配置:
餓。。R13的配置丢了。。稍等!!。。重新來配。
OK了。。3分鐘搞定!
R13#show runn
Current configuration : 2098 bytes
hostname R13
boot-start-marker
boot-end-marker
no aaa new-model
clock timezone CST 8
mmi polling-interval 60
no mmi auto-configure
no mmi pvc
mmi snmp-timeout 180
ip source-route
ip cef
no ipv6 traffic interface-statistics
no ipv6 cef
multilink bundle-name authenticated
redundancy
crypto isakmp key cisco address 23.1.1.1
set peer 23.1.1.1
ip address 23.1.1.2 255.255.255.0
ip address 2.1.1.1 255.255.255.0
ip route 1.1.1.0 255.255.255.0 23.1.1.1
access-list 110 permit ip 2.1.1.0 0.0.0.255 1.1.1.0 0.0.0.255
R14配置:
R14#show runn
Current configuration : 1680 bytes
hostname R14
ip address 2.1.1.2 255.255.255.0
ip route 0.0.0.0 0.0.0.0 2.1.1.1
R15配置:
R15#show runn
Current configuration : 2166 bytes
hostname R15
crypto isakmp key black address 25.1.1.1
set peer 25.1.1.1
no ip address
shutdown
ip address 3.1.1.1 255.255.255.0
ip address 25.1.1.2 255.255.255.0
ip route 1.1.1.0 255.255.255.0 25.1.1.1
access-list 120 permit ip 3.1.1.0 0.0.0.255 1.1.1.0 0.0.0.255
R16配置:
R16#show runn
hostname R16
ip address 3.1.1.2 255.255.255.0
ip route 0.0.0.0 0.0.0.0 3.1.1.1
!
show指令:
R12#show crypto isakmp peers
Peer: 23.1.1.2 Port: 500 Local: 23.1.1.1
Phase1 id: 23.1.1.2
Peer: 25.1.1.2 Port: 500 Local: 25.1.1.1
Phase1 id: 25.1.1.2
R12#
R13#show crypto isakmp peers
Peer: 23.1.1.1 Port: 500 Local: 23.1.1.2
Phase1 id: 23.1.1.1
R13#
R15#show crypto isakmp peers
Peer: 25.1.1.1 Port: 500 Local: 25.1.1.2
Phase1 id: 25.1.1.1
R15#
R15#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
25.1.1.1 25.1.1.2 QM_IDLE 1001 ACTIVE
IPv6 Crypto ISAKMP SA
R15#show crypto isakmp po
R15#show crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R12#show crypto isakmp policy
R12#show crypto isakmp sa
23.1.1.1 23.1.1.2 QM_IDLE 1002 ACTIVE
R12#show crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: cisco, local addr 23.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (2.1.1.0/255.255.255.0/0/0)
current_peer 23.1.1.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4
#pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 23.1.1.1, remote crypto endpt.: 23.1.1.2
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0x53578226(1398243878)
PFS (Y/N): Y, DH group: group1
inbound esp sas:
spi: 0x2D3C2A37(758917687)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 3, flow_id: SW:3, sibling_flags 80000046, crypto map: cisco
sa timing: remaining key lifetime (k/sec): (4433511/85971)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x53578226(1398243878)
conn id: 4, flow_id: SW:4, sibling_flags 80000046, crypto map: cisco
outbound ah sas:
outbound pcp sas:
interface: Ethernet0/2
Crypto map tag: black, local addr 25.1.1.1
remote ident (addr/mask/prot/port): (3.1.1.0/255.255.255.0/0/0)
current_peer 25.1.1.2 port 500
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9
#pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9
local crypto endpt.: 25.1.1.1, remote crypto endpt.: 25.1.1.2
path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/2
current outbound spi: 0x65861355(1703285589)
spi: 0x5A037DFB(1510178299)
conn id: 1, flow_id: SW:1, sibling_flags 80000046, crypto map: black
sa timing: remaining key lifetime (k/sec): (4430371/85515)
spi: 0x65861355(1703285589)
conn id: 2, flow_id: SW:2, sibling_flags 80000046, crypto map: black
=============================