一,引言
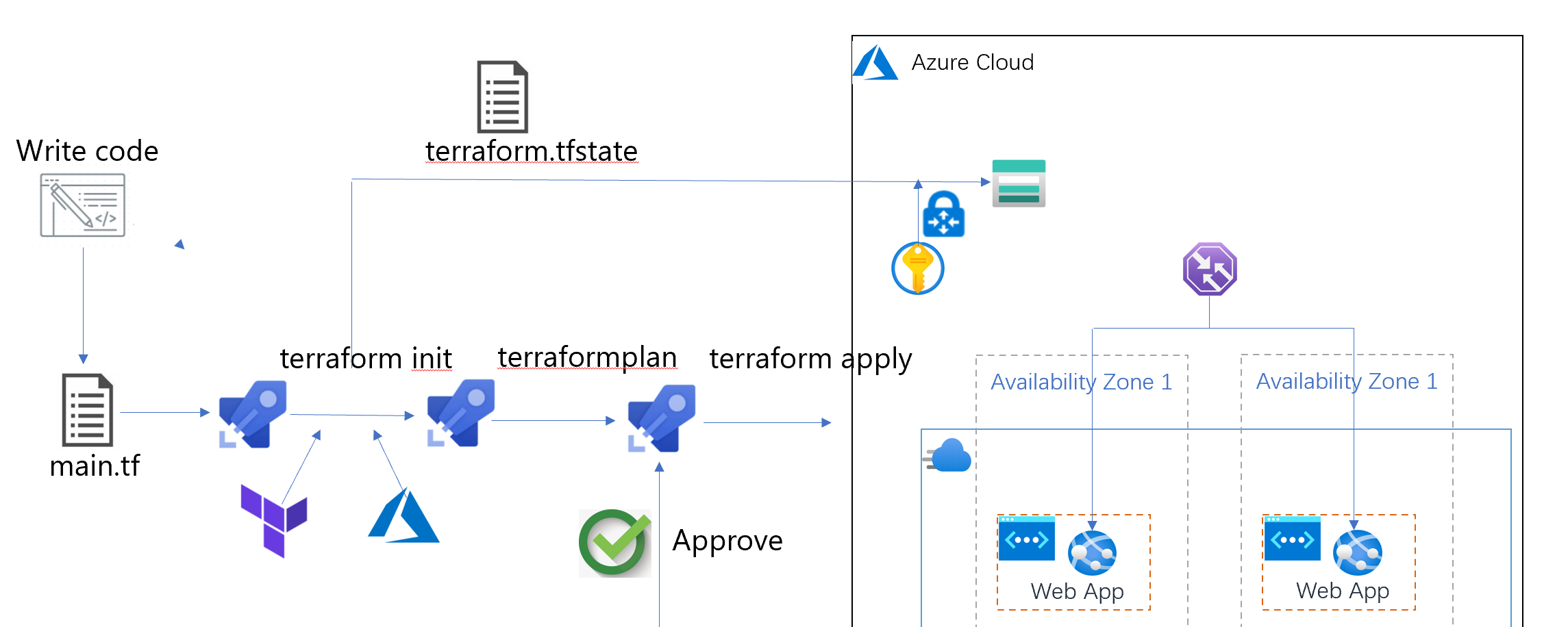
Azure Pipeline 管道是一個自動化過程;但是往往我們由于某種原因,需要在多個階段之前獲得準許之後再繼續下一步流程,是以我們可以向Azure Pipeline 管道添加審批!準許流程可幫助我們進一步控制自己的管道;我們可以控制管道内特定階段的 Step 開始,通過審批,并決定 Azure Pipeline 管道何時完成。
而至于為什麼要添加審批流程,是因為基礎設施資源的部署是需要進行評估,慎重操作。有了審批,可以檢視前一階段以确認配置代碼是否正确。
--------------------Azure Terraform 系列--------------------
1,Azure Terraform(一)入門簡介
2,Azure Terraform(二)文法詳解
3,Azure Terraform(三)部署 Web 應用程式
4,Azure Terraform(四)狀态檔案存儲
5,Azure Terraform(五)利用Azure DevOps 實作自動化部署基礎資源
6,Azure Terraform(六)Common Module
7,Azure Terraform(七)利用Azure DevOps 實作自動化部署基礎資源(補充)
8,Azure Terraform(八)利用Azure DevOps 實作Infra資源和.NET CORE Web 應用程式的持續內建、持續部署
9,Azure Terraform(九)利用 Azure DevOps Pipeline 的審批來控制流程釋出
二,正文
1,Azure DevOps 建立新的項目
登入 Azure DevOps 的位址:https://www.dev.azure.com ,點選 “+ New project” 建立新的項目
輸入項目描述等資訊
Project name:“Terraform_CnBateBlogWeb_AutoDeploy”
Visibility 選擇:“Private” ----- (根據現有項目進行設定)
Version control 選擇 “Git”
Work item process:“Agile”
确認完以上資訊,點選 “Create” 進行建立。
2,配置Azure DevOps 審批
選擇左側菜單 ”Pipelines =》Environments“,點選 ”Create environment“ 建立環境
輸入配置以下參數
Name:”Approve_AutoDeploy"
Resoure 選擇:“None” (預設即可)
點選 “Create” 建立環境
接下來為目前 “Approve_AutoDeploy” 環境建立審批
點選紅色箭頭所指,選擇 “Approve and checks” 添加審批請求
選擇 "Approvals" ,并将自己設定為申請人
添加完成後,可看到類型為 “Approvals” 的記錄,大家需要注意的是,審批的過期時間預設是 “30天”,大家可以根據實際情況更改。
3,配置 Azure DevOps Pipeline
選擇左側菜單 “Pipelines”,點選 “Create Pipeline“ 建立 管道作業
今天不使用經典編輯器模式,而選擇 GitHub (yaml)
選擇對應的 TF Code 的代碼倉庫
選擇 “Start Pipeline” 開啟新的管道建構部署代碼
Azure DevOps 會為我們自動在項目根目錄生成一個名稱叫 “azure-pipelines.yaml” 的檔案,我們将定義好的管道步驟添加到該檔案中
管道步驟審批 yaml 示例代碼
jobs:
- deployment: terraform_apply
continueOnError: false
environment: 'Approve_Production'
timeoutInMinutes: 120
strategy:
runOnce:
deploy:
steps: 注意:我将在 terraform_apply 階段之前添加一個申請請求
紅色标記是需要改成自己Azure的訂閱,
橙色标記是需要添加的變量:
1,管道變量:tf_version
2,秘密變量:terraform_rg,storage_account,storage_account_container,container_key,keyvault,keyvault_sc
1 # Starter pipeline
2 # Start with a minimal pipeline that you can customize to build and deploy your code.
3 # Add steps that build, run tests, deploy, and more:
4 # https://aka.ms/yaml
5
6 trigger:
7 - remote_stats
8
9 pool:
10 vmImage: ubuntu-latest
11
12 variables:
13 - name: tf_version
14 value: 'latest'
15
16 stages:
17 - stage: script
18 jobs:
19 - job: azure_cli_script
20 steps:
21 - task: AzureCLI@2
22 displayName: 'Azure CLI :Create Storage Account,Key Vault And Set KeyVault Secret'
23 inputs:
24 azureSubscription: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
25 scriptType: 'bash'
26 scriptLocation: 'inlineScript'
27 inlineScript: |
28 # create azure resource group
29 az group create --location eastasia --name $(terraform_rg)
30
31 # create azure storage account
32 az storage account create --name $(storage_account) --resource-group $(terraform_rg) --location eastasia --sku Standard_LRS
33
34 # create storage account container for tf state
35 az storage container create --name $(storage_account_container) --account-name $(storage_account)
36
37 # query storage key and set variable
38 ACCOUNT_KEY=$(az storage account keys list --resource-group $(terraform_rg) --account-name $(storage_account) --query "[?keyName == 'key1'][value]" --output tsv)
39
40 # create azure keyvault
41 az keyvault create --name $(keyvault) --resource-group $(terraform_rg) --location eastasia --enable-soft-delete false
42
43 # set keyvault secret,secret value is ACCOUNT_KEY
44 az keyvault secret set --name $(keyvault_sc) --vault-name $(keyvault) --value $ACCOUNT_KEY
45
46 - task: AzureKeyVault@2
47 displayName: 'Azure Key Vault :Get Storage Access Secret'
48 inputs:
49 azureSubscription: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
50 KeyVaultName: '$(keyvault)'
51 SecretsFilter: 'terraform-stste-storage-key'
52 RunAsPreJob: false
53
54 - stage: terraform_validate
55 jobs:
56 - job: terraform_validate
57 steps:
58 - task: TerraformInstaller@0
59 inputs:
60 terraformVersion: ${{variables.tf_version}}
61 - task: TerraformTaskV2@2
62 displayName: 'terraform init'
63 inputs:
64 provider: 'azurerm'
65 command: 'init'
66 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"'
67 backendServiceArm: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
68 backendAzureRmResourceGroupName: $(terraform_rg)
69 backendAzureRmStorageAccountName: $(storage_account)
70 backendAzureRmContainerName: $(storage_account_container)
71 backendAzureRmKey: $(container_key)
72 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
73 - task: TerraformTaskV2@2
74 inputs:
75 provider: 'azurerm'
76 command: 'validate'
77 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
78
79 - stage: terraform_plan
80 dependsOn: [terraform_validate]
81 condition: succeeded('terraform_validate')
82 jobs:
83 - job: terraform_plan
84 steps:
85 - task: TerraformInstaller@0
86 inputs:
87 terraformVersion: ${{ variables.tf_version }}
88 - task: TerraformTaskV2@2
89 displayName: 'terraform init'
90 inputs:
91 provider: 'azurerm'
92 command: 'init'
93 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"'
94 backendServiceArm: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
95 backendAzureRmResourceGroupName: $(terraform_rg)
96 backendAzureRmStorageAccountName: $(storage_account)
97 backendAzureRmContainerName: $(storage_account_container)
98 backendAzureRmKey: $(container_key)
99 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
100 - task: TerraformTaskV2@2
101 inputs:
102 provider: 'azurerm'
103 command: 'plan'
104 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
105 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
106
107 - stage: terraform_apply
108 dependsOn: [terraform_plan]
109 condition: succeeded('terraform_plan')
110 jobs:
111 - deployment: terraform_apply
112 continueOnError: false
113 environment: 'Approve_Production'
114 timeoutInMinutes: 120
115 strategy:
116 runOnce:
117 deploy:
118 steps:
119 - checkout: self
120 - task: TerraformInstaller@0
121 inputs:
122 terraformVersion: ${{ variables.tf_version }}
123 - task: TerraformTaskV2@2
124 displayName: 'terraform init'
125 inputs:
126 provider: 'azurerm'
127 command: 'init'
128 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"'
129 backendServiceArm: 'Microsoft Azure Subscrription(XXXX-XXX-XX-XX-XXX)'
130 backendAzureRmResourceGroupName: $(terraform_rg)
131 backendAzureRmStorageAccountName: $(storage_account)
132 backendAzureRmContainerName: $(storage_account_container)
133 backendAzureRmKey: $(container_key)
134 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
135 - task: TerraformTaskV2@2
136 inputs:
137 provider: 'azurerm'
138 command: 'plan'
139 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
140 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
141 - task: TerraformTaskV2@2
142 inputs:
143 provider: 'azurerm'
144 command: 'apply'
145 commandOptions: '-auto-approve'
146 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
147 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
148
149 # - stage: terraform_apply
150 # dependsOn: [terraform_plan]
151 # condition: succeeded('terraform_plan')
152 # jobs:
153 # - job: terraform_apply
154 # steps:
155 # - task: TerraformInstaller@0
156 # inputs:
157 # terraformVersion: ${{ variables.tf_version }}
158 # - task: TerraformTaskV2@2
159 # displayName: 'terraform init'
160 # inputs:
161 # provider: 'azurerm'
162 # command: 'init'
163 # # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"'
164 # backendServiceArm: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
165 # backendAzureRmResourceGroupName: $(terraform_rg)
166 # backendAzureRmStorageAccountName: $(storage_account)
167 # backendAzureRmContainerName: $(storage_account_container)
168 # backendAzureRmKey: $(container_key)
169 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
170 # - task: TerraformTaskV2@2
171 # inputs:
172 # provider: 'azurerm'
173 # command: 'plan'
174 # environmentServiceNameAzureRM: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
175 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
176 # - task: TerraformTaskV2@2
177 # inputs:
178 # provider: 'azurerm'
179 # command: 'apply'
180 # commandOptions: '-auto-approve'
181 # environmentServiceNameAzureRM: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
182 # workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
183
184 - stage: terraform_destroy
185 dependsOn: [terraform_apply]
186 condition: succeeded('terraform_apply')
187 jobs:
188 - job: terraform_destroy
189 steps:
190 - task: TerraformInstaller@0
191 inputs:
192 terraformVersion: ${{ variables.tf_version }}
193 - task: TerraformTaskV2@2
194 displayName: 'terraform init'
195 inputs:
196 provider: 'azurerm'
197 command: 'init'
198 # commandOptions: '-backend-config="access_key=$(terraform-stste-storage-key)"'
199 backendServiceArm: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
200 backendAzureRmResourceGroupName: $(terraform_rg)
201 backendAzureRmStorageAccountName: $(storage_account)
202 backendAzureRmContainerName: $(storage_account_container)
203 backendAzureRmKey: $(container_key)
204 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
205 - task: TerraformTaskV2@2
206 inputs:
207 provider: 'azurerm'
208 command: 'plan'
209 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
210 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/'
211 - task: TerraformTaskV2@2
212 inputs:
213 provider: 'azurerm'
214 command: 'destroy'
215 commandOptions: '-auto-approve'
216 environmentServiceNameAzureRM: 'Microsoft Azure Subscription(XXXX-XXX-XX-XX-XXX)'
217 workingDirectory: '$(System.DefaultWorkingDirectory)/src/model/' 添加秘密變量,點選 “ Variables=》New variable”
輸入機密的名稱和值
Name:“terraform_rg”
Value:“Web_Test_TF_RG”
點選 “OK” 确認添加操作
按照以上方式一次添加以下機密資訊
terraform_rg:"Web_Test_TF_RG"
storage_account:"cnbatetfstorage"
storage_account_container:"tf-state001"
container_key:"cnbate.tf.stats"
keyvault:"cnbate-terraform-kv001"
keyvault_sc:"terraform-stste-storage-key"
完成以上資訊後,點選 ”Run” 手動觸發目前 Pipeline
選擇分支 ‘“remote_stats”,點選 “Run”
接下來我們就會看到整個流程步驟,以及目前運作運作的步驟,如果需要審批,流程就會暫停,等待審批完成後,再執行後續操作
點選 “Approve” 同意審批,進行下一步執行 TF Code 執行部署計劃
OK,成功!!!部署完成。是✨😁ヾ(≧▽≦*)o
三,結尾
對于今天實驗的操作,大家可以多多練習,參考作者的 github 倉庫。今天的内容需要在Azure DevOps 上進行操作的,大家要多加練習。至于 Terraform 代碼方面沒有過多的講解,主要是因為結合之前部署Azure 資源,大家都會Terraform 有了一定的了解了。是以大家可以自行下載下傳,進行分析修改。
參考資料:Terraform 官方,Azure Pipeline 文檔
Terraform_Cnbate_Traffic_Manager github Address:https://github.com/yunqian44/Terraform_Cnbate_Traffic_Manager
歡迎大家關注部落客的部落格:https://allenmasters.com/
作者:Allen
版權:轉載請在文章明顯位置注明作者及出處。如發現錯誤,歡迎批評指正。
作者:Allen