Stores use the face recognition system to secretly obtain user information without informing users; resumes on recruitment platforms can be downloaded at will as long as they pay; mobile phone cleaning software secretly obtains information in mobile phones and profiles users...
A few days ago, the 315 party exposed the chaos of some enterprises illegally using user information for profit, so that data security issues were once again pushed to the cusp of the storm.
After the problem was exposed, the named enterprises immediately issued an apology statement and said that they would make rectifications.
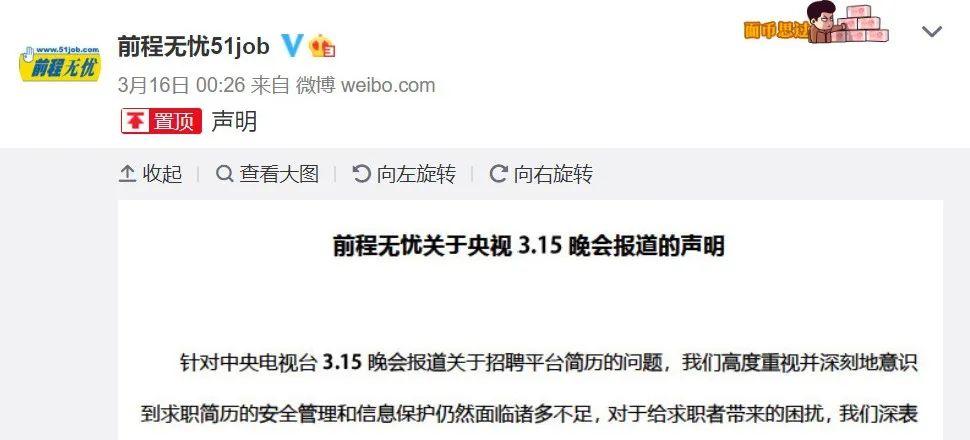
51job issued an apology overnight
But @People's Daily did not buy such an apology, saying that "the apology is a gesture, and it should be a ruminant action." If there is not enough sincerity, the apology will degenerate into a clumsy crisis pry."
Can 315 exposure drive a solution to data security issues? Maybe, but it's not enough.
For a long time in the past, data breaches have not been a new topic, nor is it the first time they have received such a lot of attention.
As far back as 16 years due to information leakage was cheated away 9900 yuan after cardiac arrest unfortunately passed away, xu Yuyu, recently last year 172 million Weibo user information was leaked, Lee Kai-fu "slip of mouth" expression layer to help Megvii Technology obtain a large number of face data from Ant Financial, Meitu, face recognition algorithm training.
Kai-Fu Lee's apology microblog after his "slip of the tongue" last year
However, the original intention of collecting data is not to sell for profit, but to build a user data model, better tap the user's behavior patterns, reduce search costs for consumers, improve life efficiency, and give consumers the most relevant choices rather than more choices.
But instead of doing the opposite, we handed over the data, didn't get the convenience we wanted, and instead gave up our privacy rights.
Currently, our data privacy is virtually unprotected. Registering an app requires our network authorization, location authorization, address book authorization, if you refuse the authorization, it will not work properly, is this what we want? Is it possible for our data to be recorded and used all the time?
We don't even know who exactly took what data we had taken and what they did with it.
Today, I would like to recommend three experts in data security-related fields, each of whom may provide you with new thinking about data security.
Let's take a look at these three experts.
Andrés Weslan is a former chief scientist at Amazon and the founder and head of the social data lab.
Wei Si'an is an expert in mobile social technology, big data and consumer behavior, and while at Amazon, he pioneered Amazon's "Guess What You Want to Buy" personalized consumer recommendation. His social media data theory provides theoretical support for the social data transformation of companies such as Alibaba.
"We should accept the reality that we don't have privacy," he said. ”
He believes that we are experiencing a social data revolution. Whatever we do, we're constantly creating data that reflects the structure of our relationships with each other.
In addition to helping individuals make better decisions, this data can also help companies make better decisions about us.
Google and Baidu have mastered the preferences of everyone in the world; Tencent and Facebook have mastered the interaction of everyone in the world; Alibaba and Amazon have mastered the transactions of everyone in the world...
The revolution is characterized by a fundamental transfer of power.
This social data revolution has fundamentally changed the way we make decisions, not just the way we make shopping decisions, but also the way we make decisions about who I am, and even the way we make decisions about what is information.
What is the Social Data Revolution?
How do you unlock the value of your data?
In the data world, can businesses achieve a win-win situation?
If you want to ask similar questions, please leave a message in the comment area at the end of the article, we will arrange a live connection, do not miss it when you walk by!
Qi Wang, founder and CEO of Keen, initiator and founder of the International Security Geek Contest geekpwn campaign, founded the first Asian team to win the world's top hacking competition, the keen team .
The keen team white hat hacker security research team he founded is the team that has found the most high-risk computer vulnerabilities in the world, providing hundreds of serious security vulnerabilities for popular software of Google, Microsoft, Apple and other companies, and is also the only partner of the top security group Google Project Zero Asia.
As a "white hat hacker", he starts from the perspective of hacking, believing that in today's digital era, it is inevitable that our information data will be transmitted, recorded, and stored.
"99% of personal privacy breaches are not caused by hackers, and only 1% of leaks are caused by hackers," he said. Of course, despite only 1%, the consequences of hacking attacks are often not to be underestimated in terms of scale and severity. ”
Wang Qi believes that security loopholes cannot be eradicated, and we have to continue to live in such an environment that is not particularly safe. But we also don't need to be pessimistic, because "security" is always a dynamic process that cannot be achieved overnight.
Are personal privacy leak cases all done by hackers?
What should we do to protect our privacy?
Will artificial intelligence bring new privacy security risks?
If you want to ask similar questions, please leave a message in the comment area at the end of the article, and we will arrange a live broadcast to discuss topics of interest to everyone.
Jia Jiaya, Tenured Professor of the Department of Computer Science Engineering, Chinese University of Hong Kong, Academician of the Institute of Electrical and Electronics Engineers, Founder of Smartmore of Symou Technology, former co-head of Tencent Youtu Lab, international authoritative expert in the fields of computer vision, artificial intelligence, computer graphics and computational imaging.
He founded Simou Technology is committed to the ai vision architecture in the field of intelligent manufacturing, ultra-high-definition video landing application, in Shenzhen and Hong Kong have set up R & D centers, with more than 300 international patents, to provide customers with full-link industrial vision AI end-to-end system of intelligent manufacturing solutions.
He pointed out that thanks to advances in facial recognition technology, an ancient type of crime, child trafficking, is gradually disintegrating by technology.
The child lost more than ten years ago, many years later, after finding someone through the official or government, we have to confirm whether this person is the person we are looking for, in addition to DNA, the simplest and intuitive way is to compare through the face.
From children to adulthood, a person's face changes may be very large, to track its change process, we need to analyze the vast majority of people's face through big data to analyze what will happen to the face, whether the face is longer or thinner, the corner of the eye is wider or narrower...
In the middle of these changes, we have to look for a kind of universality, and the process of finding universality must also rely on the provision of data.
He also admitted that face recognition will definitely bring security risks, at the application level, how to prevent the abuse of face information, prevent data or algorithms from being used in bad scenarios, and prevent criminals from using technology to generate false faces to steal bank information online, etc., all need to be solved urgently.
What does cross-age face recognition technology rely on?
How to view the data security risks brought about by face recognition?
At present, what is the most urgent technical difficulty for face recognition technology to be broken?
If you want to ask similar questions, please leave a message in the comment area at the end of the article, we will arrange a live connection, do not miss it!
The Shaping Project invites everyone's favorite guests to share online live broadcasts and discuss how to protect our privacy in the digital age.
Which guest would you most like to hear from to analyze what aspect of the problem? Everyone is welcome to speak enthusiastically in the comments section, pick up your favorite guests, and leave your concerns.
(Reprinting of this article without authorisation is prohibited.) )
Edit & Layout | Xiao Na