在使用應用程式通路Key Vault擷取密鑰資訊時,現後遇見了多種認證錯誤。使用的代碼為:
String keyVaultUrl = "https://test-xxx.vault.azure.cn/"
String keyName = "keyvault-xxx";
KeyClient keyClient = new KeyClientBuilder()
.vaultUrl(keyVaultUrl)
.credential(new DefaultAzureCredentialBuilder()
.tenantId("3c858e6a-xxxx-xxxx-xxxx-xxxxxxxxxxxx")
.managedIdentityClientId("3df5246c-xxxx-xxxx-xxxx-xxxxxxxxxxxx")
.build())
.buildClient();
KeyVaultKey key = keyClient.getKey(keyName); 遇見的錯誤一:
Error Details: AADSTS90002: Tenant '3c858e6a-xxxx-xxxx-xxxx-xxxxxxxxxxxx' not found. This may happen if there are no active subscriptions for the tenant. Check to make sure you have the correct tenant ID. Check with your subscription administrator
錯誤分析:
根據Key Vaule的URL判斷,服務位于中國區的Azure中,由于中國區的Azure和Globa Azure是兩個獨立的雲環境,是以在使用SDK登入中國區Azure環境時,需要指定Authority Host。是以需要在代碼中加入 " .authorityHost(AzureAuthorityHosts.AZURE_CHINA) “。
修改後的代碼為:
String keyVaultUrl = "https://test-xxx.vault.azure.cn/"
String keyName = "keyvault-xxx";
KeyClient keyClient = new KeyClientBuilder()
.vaultUrl(keyVaultUrl)
.credential(new DefaultAzureCredentialBuilder()
.tenantId("3c858e6a-xxxx-xxxx-xxxx-xxxxxxxxxxxx")
.authorityHost(AzureAuthorityHosts.AZURE_CHINA)
.managedIdentityClientId("3df5246c-xxxx-xxxx-xxxx-xxxxxxxxxxxx")
.build())
.buildClient();
KeyVaultKey key = keyClient.getKey(keyName); 遇見的錯誤二:
IntelliJ Authentication not available. Please log in with Azure Tools for IntelliJ plugin in the IDE
Status code 403, "{"error":{"code":"Forbidden","message":"The policy requires the caller 'appid=60015a25-xxxx-xxxx-xxxx-xxxxxxxxxxxx;oid=dc107e73-xxxx-xxxx-xxxx-xxxxxxxxxxxx;iss=https://sts.chinacloudapi.cn/3c858e6a-xxxx-xxxx-xxxx-xxxxxxxxxxxx/' to use on-behalf-of (OBO) flow. For more information on OBO, please see https://go.microsoft.com/fwlink/?linkid=2152310","innererror":{"code":"ForbiddenByPolicy"}}}"
因為通路Azure Key Vault需要添加通路政策,需要為目前使用的 Client ID (3df5246c-xxxx-xxxx-xxxx-xxxxxxxxxxxx)配置 通路政策[Access Policy]
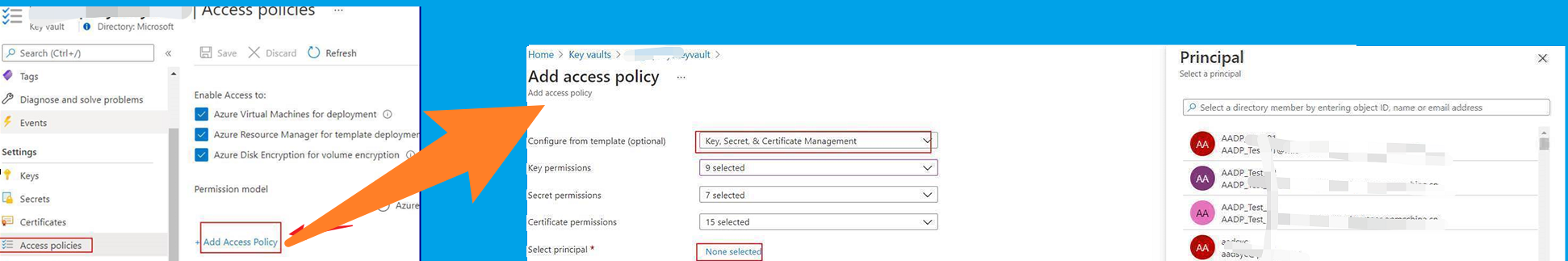
遇見的錯誤三:
認證主題不是自定義的AAD注冊應用,而是服務主體(Service Principal) , 是以需要使用 ClientSecretCredential 對象進行認證,而不是預設的 DefaultAzureCredentialBuilder 。
使用ClientSecretCredential 認證的參考代碼為:
/**
* Authenticate with client secret.
*/
ClientSecretCredential clientSecretCredential = new ClientSecretCredentialBuilder()
.clientId("<your client ID>")
.clientSecret("<your client secret>")
.tenantId("<your tenant ID>")
.authorityHost(AzureAuthorityHosts.AZURE_CHINA)
.build();
// Azure SDK client builders accept the credential as a parameter.
SecretClient client = new SecretClientBuilder()
.vaultUrl("https://<your Key Vault name>.vault.azure.net")
.credential(clientSecretCredential)
.buildClient(); 參考資料:
Client secret credential:https://docs.microsoft.com/en-us/azure/developer/java/sdk/identity-service-principal-auth#client-secret-credential
對 Azure 托管的 Java 應用程式進行身份驗證: https://docs.microsoft.com/zh-cn/azure/developer/java/sdk/identity-azure-hosted-auth
當在複雜的環境中面臨問題,格物之道需:濁而靜之徐清,安以動之徐生。 雲中,恰是如此!