K8S的web管理方式-dashboard
目錄
-
- 1 部署dashboard
-
-
- 1.1 擷取dashboard鏡像
-
-
-
-
- 1.1.1 擷取1.8.3版本的dsashboard
- 1.1.2 擷取1.10.1版本的dashboard
- 1.1.3 為何要兩個版本的dashbosrd
-
-
-
-
- 1.2 建立dashboard資源配置清單
-
-
-
-
- 1.2.1 建立rbca授權清單
- 1.2.2 建立depoloy清單
- 1.2.3 建立service清單
- 1.2.4 建立ingress清單暴露服務
-
-
-
-
- 1.3 建立相關資源
-
-
-
-
- 1.3.1 在任意node上建立
- 1.3.2 添加域名解析
- 1.3.3 通過浏覽器驗證
-
-
-
- 2 更新dashboard版本
-
-
- 2.1 把版本換成1.10以上版本
-
-
-
-
- 2.1.1 線上修改直接使用
- 2.2.2 等待滾動釋出
- 2.2.3 重新整理dashboard頁面:
-
-
-
-
- 2.2 使用token登入
-
-
-
-
- 2.2.1 首先擷取secret資源清單
- 2.2.2 擷取角色的詳情
- 2.2.3 申請證書
- 2.2.4 前端nginx服務部署證書
- 2.2.5 再次登入dashboard
-
-
-
-
- 2.3 授權細則思考
-
dashboard是k8s的可視化管理平台,是三種管理k8s叢集方法之一
擷取鏡像和建立資源配置清單的操作,還是老規矩:
7.200
上操作
docker pull k8scn/kubernetes-dashboard-amd64:v1.8.3
docker tag k8scn/kubernetes-dashboard-amd64:v1.8.3 harbor.zq.com/public/dashboard:v1.8.3
docker push harbor.zq.com/public/dashboard:v1.8.3 docker pull loveone/kubernetes-dashboard-amd64:v1.10.1
docker tag loveone/kubernetes-dashboard-amd64:v1.10.1 harbor.zq.com/public/dashboard:v1.10.1
docker push harbor.zq.com/public/dashboard:v1.10.1 .1.3 為何要兩個版本的dashbosrd
- 1.8.3版本授權不嚴格,友善學習使用
- 1.10.1版本授權嚴格,學習使用麻煩,但生産需要
mkdir -p /data/k8s-yaml/dashboard cat >/data/k8s-yaml/dashboard/rbac.yaml <<EOF
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
name: kubernetes-dashboard-admin
namespace: kube-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: kubernetes-dashboard-admin
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
addonmanager.kubernetes.io/mode: Reconcile
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: kubernetes-dashboard-admin
namespace: kube-system
EOF cat >/data/k8s-yaml/dashboard/dp.yaml <<EOF
apiVersion: apps/v1
kind: Deployment
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
matchLabels:
k8s-app: kubernetes-dashboard
template:
metadata:
labels:
k8s-app: kubernetes-dashboard
annotations:
scheduler.alpha.kubernetes.io/critical-pod: ''
spec:
priorityClassName: system-cluster-critical
containers:
- name: kubernetes-dashboard
image: harbor.zq.com/public/dashboard:v1.8.3
resources:
limits:
cpu: 100m
memory: 300Mi
requests:
cpu: 50m
memory: 100Mi
ports:
- containerPort: 8443
protocol: TCP
args:
# PLATFORM-SPECIFIC ARGS HERE
- --auto-generate-certificates
volumeMounts:
- name: tmp-volume
mountPath: /tmp
livenessProbe:
httpGet:
scheme: HTTPS
path: /
port: 8443
initialDelaySeconds: 30
timeoutSeconds: 30
volumes:
- name: tmp-volume
emptyDir: {}
serviceAccountName: kubernetes-dashboard-admin
tolerations:
- key: "CriticalAddonsOnly"
operator: "Exists"
EOF cat >/data/k8s-yaml/dashboard/svc.yaml <<EOF
apiVersion: v1
kind: Service
metadata:
name: kubernetes-dashboard
namespace: kube-system
labels:
k8s-app: kubernetes-dashboard
kubernetes.io/cluster-service: "true"
addonmanager.kubernetes.io/mode: Reconcile
spec:
selector:
k8s-app: kubernetes-dashboard
ports:
- port: 443
targetPort: 8443
EOF cat >/data/k8s-yaml/dashboard/ingress.yaml <<EOF
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: kubernetes-dashboard
namespace: kube-system
annotations:
kubernetes.io/ingress.class: traefik
spec:
rules:
- host: dashboard.zq.com
http:
paths:
- backend:
serviceName: kubernetes-dashboard
servicePort: 443
EOF kubectl create -f http://k8s-yaml.zq.com/dashboard/rbac.yaml
kubectl create -f http://k8s-yaml.zq.com/dashboard/dp.yaml
kubectl create -f http://k8s-yaml.zq.com/dashboard/svc.yaml
kubectl create -f http://k8s-yaml.zq.com/dashboard/ingress.yaml vi /var/named/zq.com.zone
dashboard A 10.4.7.10
# 注意前滾serial編号
systemctl restart named 在本機浏覽器上通路
http://dashboard.zq.com
,如果出來web界面,表示部署成功
可以看到安裝1.8版本的dashboard,預設是可以跳過驗證的:
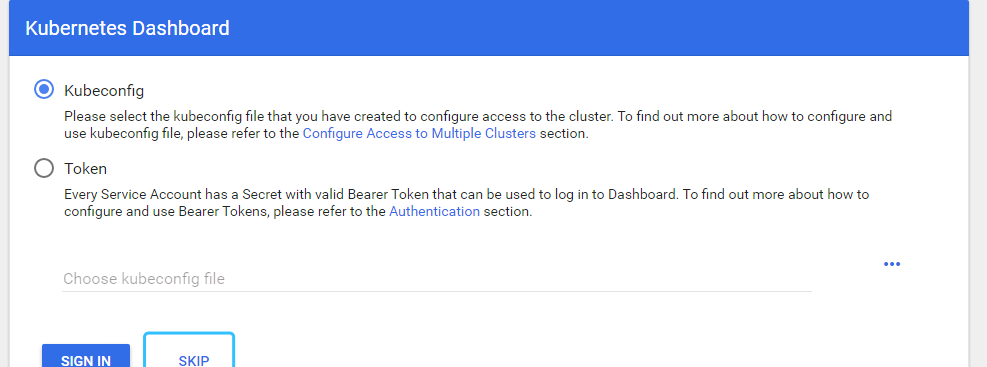
跳過登入是不科學的,因為我們在配置dashboard的rbac權限時,綁定的角色是system:admin,這個是叢集管理者的角色,權限很大,如果任何人都可跳過登入直接使用,那你就等着背鍋吧
在前面我們已經同時下載下傳了1.10.1版本的docker鏡像
kubectl edit deploy kubernetes-dashboard -n kube-system [root@hdss7-21 ~]# kubectl -n kube-system get pod|grep dashboard
kubernetes-dashboard-5bccc5946b-vgk5n 1/1 Running 0 20s
kubernetes-dashboard-b75bfb487-h7zft 0/1 Terminating 0 2m27s
[root@hdss7-21 ~]# kubectl -n kube-system get pod|grep dashboard
kubernetes-dashboard-5bccc5946b-vgk5n 1/1 Running 0 52s 可以看到這裡原來的skip跳過已經沒有了,我們如果想登陸,必須輸入token,那我們如何擷取token呢:
2.2.1 首先擷取 secret
secret
kubectl get secret -n kube-system 清單中有很多角色,不同到角色有不同的權限,找到想要的角色
dashboard-admin
後,再用describe指令擷取詳情
kubectl -n kube-system describe secrets kubernetes-dashboard-admin-token-85gmd 找到詳情中的token字段,就是我們需要用來登入的東西
拿到token去嘗試登入,發現仍然登入不了,因為必須使用https登入,是以需要申請證書
申請證書在
7.200
主機上
建立json檔案:
cd /opt/certs/
cat >/opt/certs/dashboard-csr.json <<EOF
{
"CN": "*.zq.com",
"hosts": [
],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "beijing",
"L": "beijing",
"O": "zq",
"OU": "ops"
}
]
}
EOF 申請證書
cfssl gencert -ca=ca.pem \
-ca-key=ca-key.pem \
-config=ca-config.json \
-profile=server \
dashboard-csr.json |cfssl-json -bare dashboard 檢視申請的證書
[root@hdss7-200 certs]# ll |grep dash
-rw-r--r-- 1 root root 993 May 4 12:08 dashboard.csr
-rw-r--r-- 1 root root 280 May 4 12:08 dashboard-csr.json
-rw------- 1 root root 1675 May 4 12:08 dashboard-key.pem
-rw-r--r-- 1 root root 1359 May 4 12:08 dashboard.pem 在
7.11
,
7.12
兩個前端代理上,都做相同操作
拷貝證書:
mkdir /etc/nginx/certs
scp 10.4.7.200:/opt/certs/dashboard.pem /etc/nginx/certs
scp 10.4.7.200:/opt/certs/dashboard-key.pem /etc/nginx/certs 建立nginx配置
cat >/etc/nginx/conf.d/dashboard.zq.com.conf <<'EOF'
server {
listen 80;
server_name dashboard.zq.com;
rewrite ^(.*)$ https://${server_name}$1 permanent;
}
server {
listen 443 ssl;
server_name dashboard.zq.com;
ssl_certificate "certs/dashboard.pem";
ssl_certificate_key "certs/dashboard-key.pem";
ssl_session_cache shared:SSL:1m;
ssl_session_timeout 10m;
ssl_ciphers HIGH:!aNULL:!MD5;
ssl_prefer_server_ciphers on;
location / {
proxy_pass http://default_backend_traefik;
proxy_set_header Host $http_host;
proxy_set_header x-forwarded-for $proxy_add_x_forwarded_for;
}
}
EOF 重新開機nginx服務
nginx -t
nginx -s reload 重新整理頁面後,再次使用前面的token登入,可以成功登入進去了
登入是登入了,但是我們要思考一個問題,我們使用rbac授權來通路dashboard,如何做到權限精細化呢?比如開發,隻能看,不能摸,不同的項目組,看到的資源應該是不一樣的,測試看到的應該是測試相關的資源